Category: HelpnetSecurity
Credential stuffing attacks have exploded this April, Okta warns, and advises its customers to use available tools to block access…
Researchers have found two novel types of attacks that target the conditional branch predictor found in high-end Intel processors, which…
The Department of Homeland Security announced the establishment of the Artificial Intelligence Safety and Security Board (the Board). The Board…
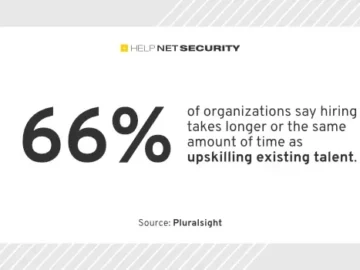
The list of skills technologists and organizations need to succeed grows with each new tech advancement, according to Pluralsight. But…
Prompt Fuzzer is an open-source tool that evaluates the security of your GenAI application’s system prompt against dynamic LLM-based threats….
Most businesses see offensive AI fast becoming a standard tool for cybercriminals, with 93% of security leaders expecting to face…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Hackers backdoored Cisco ASA devices…
Bitwarden surveyed 2,400 individuals from the US, UK, Australia, France, Germany, and Japan to investigate current user password practices. The…
LSA Whisperer consists of open-source tools designed to interact with authentication packages through their unique messaging protocols. Support is currently…
Here’s a list of interesting cybersecurity companies that received funding so far in 2024. Aim Security January | $10 million…
Here’s a look at the most interesting products from the past week, featuring releases from Cyberint, Forcepoint, Invicti Security, Netwrix,…
The Federal Communications Commission (FCC) today voted to restore a national standard to ensure the internet is fast, open, and…