Category: HelpnetSecurity
Companies demonstrating advanced cybersecurity performance generate a shareholder return that is 372% higher than their peers with basic cybersecurity performance,…
Though generative AI offers financial firms remarkable business and cybersecurity utility, cyberthreats relating to GenAI in financial services are a…
Enterprises spend enormous effort fixing software vulnerabilities that make their way into their publicly-facing applications. The Consortium for Information and…
Here’s a look at the most interesting products from the past week, featuring releases from Bedrock Security, CyberArk, GitGuardian, Legit…
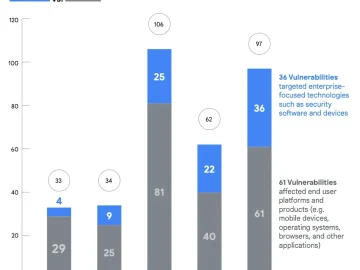
2023 saw attackers increasingly focusing on the discovery and exploitation of zero-day vulnerabilities in third-party libraries (libvpx, ImagelO) and drivers…
NHS Dumfries and Galloway (part of NHS Scotland) has confirmed that a “recognised ransomware group” was able to “access a…
Despite recent economic fluctuations, the software-as-a-service (SaaS) market isn’t letting up. The industry is set to grow annually by over…
Enterprises must secure a transformation driven by generative AI (GenAI) bidirectionally: by securely adopting GenAI tools in the enterprise with…
The majority of cyberattacks against organizations are perpetrated via social engineering of employees, and criminals are using new methods including…
The rise in identity-based attacks can be attributed to a rapid increase in malware, according to SpyCloud. Researchers found that…
Scammers are leveraging the Darcula phishing-as-a-service platform, iMessages and Google Messages to great effect. The platform allows them to impersonate…
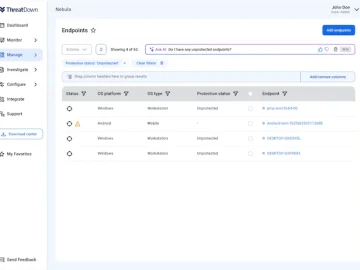
Malwarebytes has added AI functionality to its Security Advisor, available in every ThreatDown Bundle. Leveraging generative AI technology, the new…