Category: HelpnetSecurity
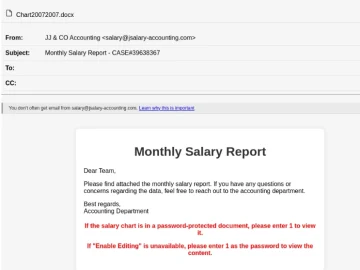
Customers of bankrupt crypto platform BlockFi have been targeted with a very convincing phishing email impersonating the platform, asking them…
Among Gartner’s top predictions are the collapse of the cybersecurity skills gap and the reduction of employee-driven cybersecurity incidents through…
Open-source software’s adaptive nature ensures its durability, relevance, and compatibility with new technologies. When I started digging deeper into the…
Scams directly targeting consumers continue to increase in both complexity and volume, according to Visa. Consumers are increasingly targeted by…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Outsmarting cybercriminal innovation with strategies…
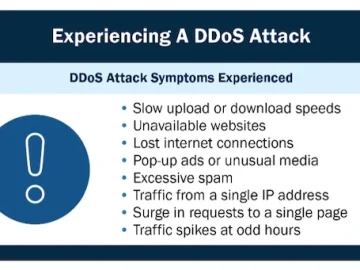
In light of the rise of “DDoS hacktivism” and the recent DDoS attacks aimed at disrupting French and Alabama government…
Employees at US-based organizations are being targeted with emails delivering NetSupport RAT malware via “nuanced” exploitation and by using an…
Despite the critical role of APIs, the vast majority of commercial decision-makers are ignoring the burgeoning security risk for businesses,…
Shadow IT – the use of software, hardware, systems and services that haven’t been approved by an organization’s IT/IT Sec…
Financially motivated hackers have been leveraging SmokeLoader malware in a series of phishing campaigns predominantly targeting Ukrainian government and administration…
The use of hybrid multicloud models is forecasted to double over the next one to three years as IT decision…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, Drata, GlobalSign, Ordr, Portnox,…