Category: HelpnetSecurity
Apricorn released a 24TB version of its Aegis Padlock DT and Padlock DT FIPS Desktop Drives. Apricorn brings a 24TB…
93% of IT professionals believe security threats are increasing in volume or severity, a significant rise from 47% last year,…
Attackers are exploiting the recently patched JetBrains TeamCity auth bypass vulnerability (CVE-2024-27198) to deliver ransomware, cryptominers and remote access trojans…
WebCopilot is an open-source automation tool that enumerates a target’s subdomains and discovers bugs using various free tools. It simplifies…
Amid the constant drumbeat of successful cyberattacks, some fake data breaches have also cropped up to make sensational headlines. Unfortunately,…
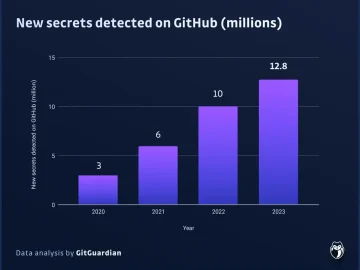
Leaked secrets, a phenomenon known as ‘secrets sprawl,’ is a pervasive vulnerability that plagues nearly every organization. It refers to…
Ivanti has fixed a critical RCE vulnerability (CVE-2023-41724) in Ivanti Standalone Sentry that has been reported by researchers with the…
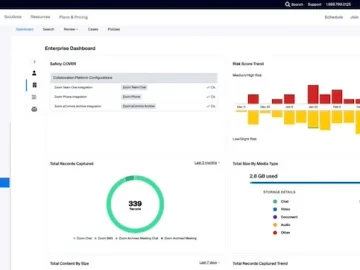
Zoom announces Zoom Compliance Manager, an all-in-one offering that provides archiving, eDiscovery, legal hold, and information protection capabilities to help…
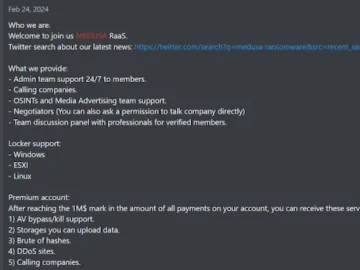
Smaller RaaS groups are trying to recruit new and “displaced” LockBit and Alphv/BlackCat affiliates by foregoing deposits and paid subscriptions,…
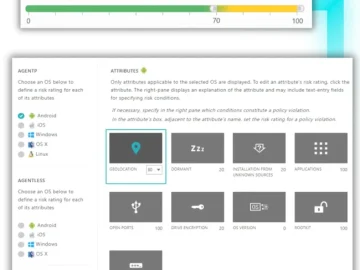
Portnox introduced its Conditional Access for Applications solution. Available as part of the Portnox Cloud platform, Conditional Access for Applications…
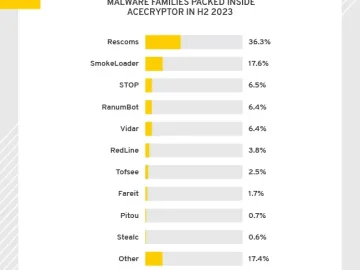
ESET Research has recorded a considerable increase in AceCryptor attacks, with detections tripling between the first and second halves of…
According to the UAE Cybersecurity Council, in 2023, the UAE repelled over 50,000 cyberattacks daily. These findings, highlighted in a…