Category: HelpnetSecurity
Data loss is a problem stemming from the interaction between humans and machines, and ‘careless users’ are much more likely…
As AI gets baked into enterprise tech stacks, AI applications are becoming prime targets for cyber attacks. In response, many…
A total of 29% of web attacks targeted APIs over 12 months (January through December 2023), indicating that APIs are…
Appdome has unveiled its new Social Engineering Prevention service on the Appdome platform. The new service enables mobile brands to…
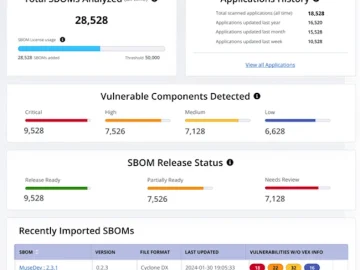
Working with the world’s largest enterprises and global policymakers to address the complexities of optimizing your software supply chain with…
Whether the cause is insurmountable technical debt, lack of funds, a third reason or all of them, NIST’s National Vulnerability…
Verimatrix released its new Verimatrix Counterspy anti-piracy solution. Counterspy leverages technology first developed by the company’s cybersecurity team back in…
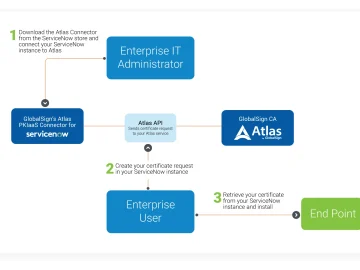
GlobalSign has unveiled the availability of the latest iteration of its PKIaaS Connector for ServiceNow. The updates to the GlobalSign…
Central Investigations & Cybersecurity Analyst Meta | USA | On-site – View job details The successful candidate will be able…
In the past few years, an increasing number of tech companies, organizations, and even governments have been working on one…
In this Help Net Security interview, Pedro Cameirão, Head of Cyber Defense Center at Nokia, discusses emerging cybersecurity trends for…
Fujitsu Limited, the largest Japanese IT services provider, has announced that several of the company’s computers have been compromised with…