Category: HelpnetSecurity
Nissan Oceania has confirmed that the data breach it suffered in December 2023 affected around 100,000 individuals and has begun…
French national unemployment agency France Travail (formerly Pôle emploi) and Cap emploi, a government employment service for people with disabilities,…
Quicmap is a fast, open-source QUIC service scanner that streamlines the process by eliminating multiple tool requirements. It effectively identifies…
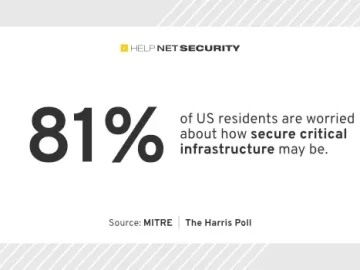
With temporary failures of critical infrastructure on the rise in the recent years, 81% of US residents are worried about…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Transitioning to memory-safe languages: Challenges…
Cyber threats are growing at an unprecedented pace, and the year ahead is fraught with cybercrime and incidents anticipated ahead…
12.8 million new secrets occurrences were leaked publicly on GitHub in 2023, +28% compared to 2022, according to GitGuardian. Remarkably,…
While the threat landscape continues to shift and evolve, attackers’ motivations do not, according to a Red Canary report. The…
Here’s a look at the most interesting products from the past week, featuring releases from AuditBoard, Cynerio, DataDome, Regula, and…
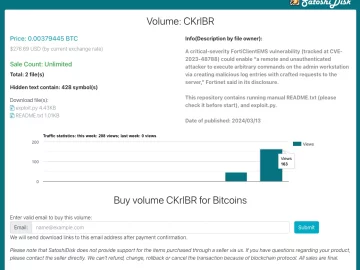
A recently fixed SQL injection vulnerability (CVE-2023-48788) in Fortinet’s FortiClient Endpoint Management Server (EMS) solution has apparently piqued the interest…
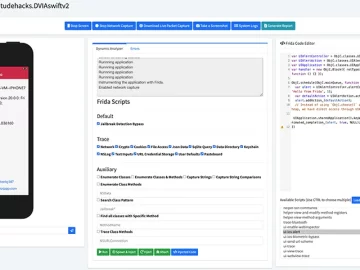
The Mobile Security Framework (MobSF) is an open-source research platform for mobile application security, encompassing Android, iOS, and Windows Mobile….
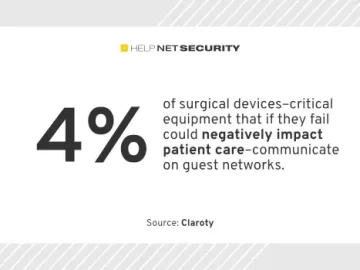
63% of CISA-tracked Known Exploited Vulnerabilities (KEVs) can be found on healthcare networks, while 23% of medical devices—including imaging devices,…