Category: HelpnetSecurity
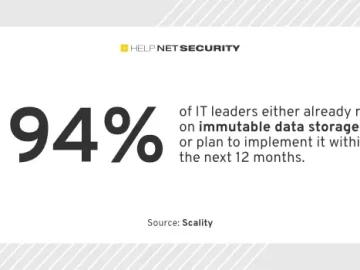
IT leaders consider immutable storage as a must-have in the fight against cyberattacks, according to Scality. Ransomware threats are now…
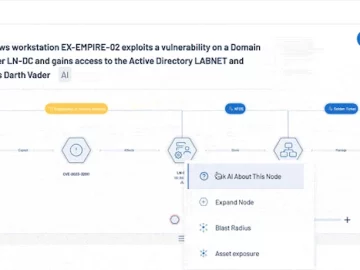
Tenable has unveiled enhancements to ExposureAI, the generative AI capabilities and services within its Tenable One Exposure Management Platform. The…
While the results of law enforcement action against ransomware-as-a-service operators Alphv/BlackCat and LockBit are yet to be fully realized, the…
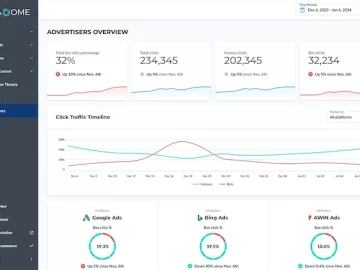
DataDome launched DataDome Ad Protect, designed to combat fraudulent traffic affecting digital ad campaigns. This solution is set to transform…
The International Organization for Migration reports that the migrant flow has been steadily rising, with the numbers swelling from 153…
Recently, LastPass appointed Asad Siddiqui as its CIO. He brings over two decades of experience leading startups and large technology…
Many wireless headsets using Bluetooth technology have vulnerabilities that may allow malicious individuals to covertly listen in on private conversations,…
In 2023, 50% of malware detections for SMBs were keyloggers, spyware and stealers, malware that attackers use to steal data…
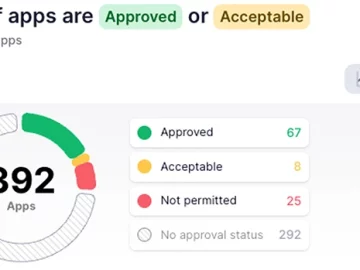
As technology adoption has shifted to be employee-led, IT and security teams are contending with an ever-expanding SaaS attack surface….
On this March 2024 Patch Tuesday, Microsoft has released fixes for 59 CVE-numbered vulnerabilities, but – welcome news! – none…
A financially motivated threat actor is using known vulnerabilities to target public-facing services and deliver custom malware to unpatched Windows…
CISO / Head of Enterprise IT Stitch Fix | USA | Remote – View job details Reporting directly to the…