Category: HelpnetSecurity
“At the most basic level, AI has given malicious attackers superpowers,” Mackenzie Jackson, developer and security advocate at GitGuardian, told…
In this Help Net Security interview, Sanjay Macwan, CIO and CISO at Vonage, addresses emerging threats to cloud communications and…
MITRE now offers an open-source version of its Aviation Risk Identification and Assessment (ARIA) software suite, OpenARIA. This initiative is…
Here’s a look at the most interesting products from the past week, featuring releases from Check Point, Delinea, Pentera, and…
VMware has fixed four vulnerabilities (CVE-2024-22252, CVE-2024-22253, CVE-2024-22254, CVE-2024-22255) in ESXi, Workstation, Fusion and Cloud Foundation, some of which could…
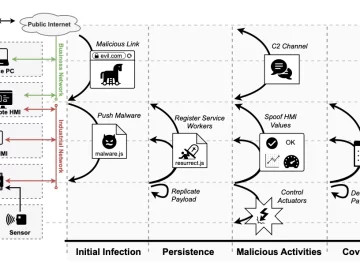
A group of researchers from Georgia Tech’s College of Engineering have developed web-based programmable logic controller (PLC) malware able to…
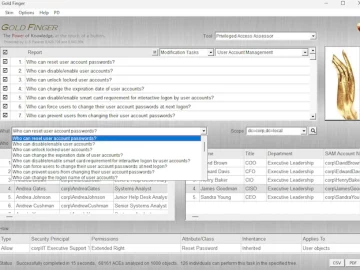
Paramount Defenses released Gold Finger version 8.0 for Microsoft Active Directory. From America to Israel, from the European Union to…
98% of companies surveyed view some of their AI models as vital for business success, and 77% have experienced breaches…
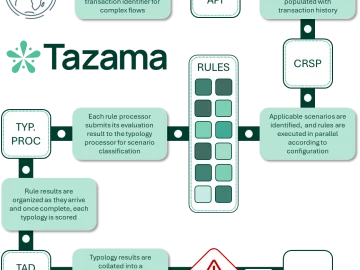
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in…
Cybersecurity remained a top priority and an area of growth for MSPs, with 73% saying it’s a top revenue driver…
The darknet is home to many underground hacking forums in which cybercriminals convene, freely sharing stories, tactics, success stories and…
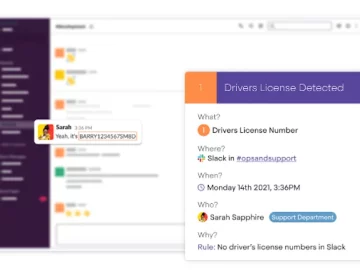
Metomic announced Metomic for Slack Enterprise. By partnering with Slack, Metomic gives security teams full visibility and control of sensitive…