Category: HelpnetSecurity
In this Help Net Security interview, Geoffrey Mattson, CEO of Xage Security, discusses the evolution of the Joint Cyber Defense…
According to the updated SEC regulations on cybersecurity incident disclosure, findings by SecurityScorecard reveal that 98% of companies are associated…
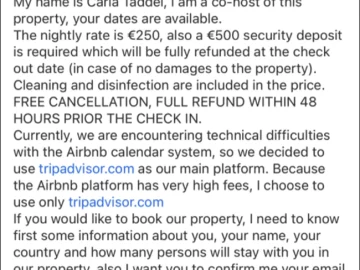
Scammers on Airbnb are faking technical issues and citing higher fees to get users to a spoofed Tripadvisor website and…
The ALPHV/BlackCat ransomware group has claimed responsibility for the cyberattack that targeted Optum, a subsidiary of UnitedHealth Group (UHG), causing…
Here’s a look at the most interesting products from the past month, featuring releases from: Appdome, BackBox, Center for Internet…
SaaS sprawl introduces security risks, operational headaches, and eye-popping subscription costs. Download this guide to learn how to implement a…
OffSec has released Kali Linux 2024.1, the latest version of its popular penetration testing and digital forensics platform. The new…
76% of enterprises lack sufficient voice and messaging fraud protection as AI-powered vishing and smishing skyrocket following the launch of…
Managing IAM challenges in hybrid IT environments requires a holistic approach, integrating solutions and automating processes to ensure effective access…
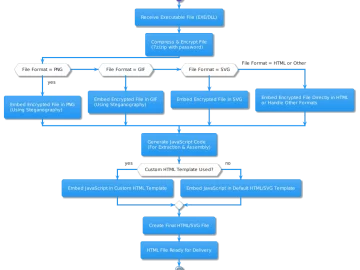
BobTheSmuggler is an open-source tool designed to easily compress, encrypt, and securely transport your payload. It basically enables you to…
As commercial adoption of cloud technologies continues, cloud-focused malware campaigns have increased in sophistication and number – a collective effort…
Pepco Group has confirmed that its Hungarian business has been hit by a “sophisticated fraudulent phishing attack.” The European company,…