Category: HelpnetSecurity
A blind SQL injection vulnerability (CVE-2023-51448) in Cacti, a widely-used network monitoring, performance and fault management framework, could lead to…
Why is it that when a company becomes aware of a potential data security incident, the team working on it…
In this Help Net Security interview, Phil Vachon, Head of Infrastructure in the Office of the CTO at Bloomberg, discusses…
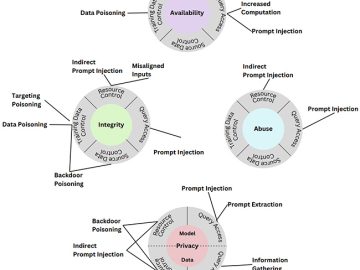
Adversaries can intentionally mislead or “poison” AI systems, causing them to malfunction, and developers have yet to find an infallible…
Andrew Ginter is a widely-read author on industrial security and a trusted advisor for industrial enterprises. He holds a BSc….
In this Help Net Security interview, Jayson E. Street, Chief Adversarial Officer at Secure Yeti, discusses intriguing aspects of social…
AuthLogParser is an open-source tool tailored for digital forensics and incident response, specifically crafted to analyze Linux authentication logs (auth.log)….
Vim, a highly adaptable text editor, is designed to efficiently create and modify all types of text. It comes included…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Wi-Fi 7’s mission-critical role in…
Happy 2024 Everyone! I hope everyone is looking forward to another exciting year in the ever-changing world of IT operations…
The motivations behind cyberattacks are as diverse as the methods employed. Whether driven by financial gain, political agendas, or sheer…
60% of IT decision-makers agreed that budget cuts have negatively impacted their mental health and wellbeing, according to Integrity360. To…