Category: HelpnetSecurity
VMware Enhanced Authentication Plug-in (EAP), a plugin for VMware vSphere, has two vulnerabilities (CVE-2024-22245, CVE-2024-22250) that could be exploited by…
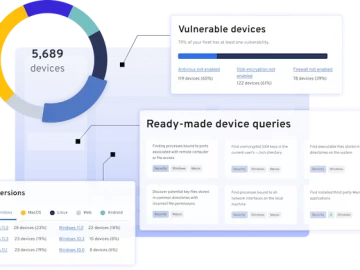
Beyond Identity released a new Device360 solution for continuous device security posture management. Device360 is the device security tool designed…
Check Point introduces Check Point Quantum Force series: a lineup of ten firewalls designed to meet and exceed the stringent…
Nearly every organization has core systems services tied to Active Directory that will go down during an outage, according to…
In 2024, API requests accounted for 57% of dynamic internet traffic around the globe, according to the Cloudflare 2024 API…
At Help Net Security, we’ve been following the cybersecurity business landscape closely for the past 25 years. Through our Industry…
TruffleHog is an open-source scanner that identifies and addresses exposed secrets throughout your entire technology stack. “TruffleHog was originally a…
A Ukrainian national was extradited to the United States from the Netherlands after being indicted for crimes related to fraud,…
On Monday afternoon, LockBit’s leak site has been taken over by a coalition of law enforcement agencies and is showing…
In the wake of yesterday’s surprise law enforcement takeover of LockBit’s leak site, the UK National Crime Agency (NCA) and…
Analysis of 7 billion emails shows clean links are duping users, malicious EML attachments increased 10-fold in Q4, and social…
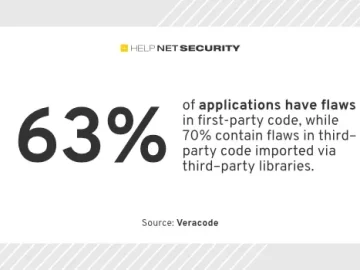
Security debt, defined as flaws that remain unfixed for longer than a year, exists in 42% of applications and 71%…