Category: HelpnetSecurity
Despite the importance of security, it was, until recently, an afterthought in building design, according to Brivo. Rather than considering…
German battery manufacturer Varta was forced to shut down its IT systems and stop production as a result of a…
CompliancePro Solutions launched their new analytics product, CPS Insights. As a new add-on module to the CompliancePro Privacy Program Management…
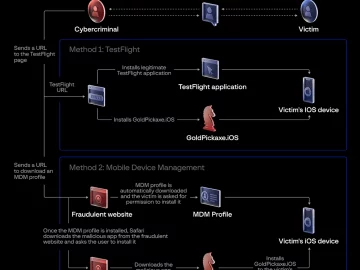
Group-IB uncovered a new iOS trojan designed to steal users’ facial recognition data, identity documents, and intercept SMS. The trojan,…
Picus Security has revealed a rise in hunter-killer malware, highlighting a significant shift in adversaries’ capability to pinpoint and thwart…
In an era of artificial intelligence (AI) revolutionizing business practices, many companies are turning to third-party AI services for a…
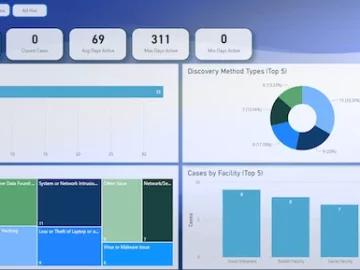
Digital forensics plays a crucial role in analyzing and addressing cyberattacks, and it’s a key component of incident response. Additionally,…
Shipments of AI PCs – personal computers with specific system-on-a-chip (SoC) capabilities designed to run generative AI tasks locally –…
Microsoft and OpenAI have identified attempts by various state-affiliated threat actors to use large language models (LLMs) to enhance their…
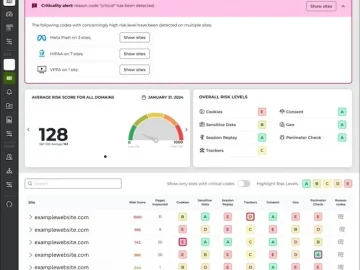
LOKKER introduces a new feature included in its Privacy Edge software suite. LOKKER now gives companies a solution to monitor…
QNAP Systems has patched two unauthenticated OS command injection vulnerabilities (CVE-2023-47218, CVE-2023-50358) in various versions of the operating systems embedded…
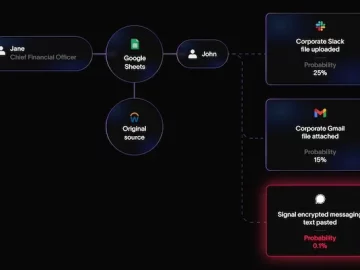
Cyberhaven launched Linea AI, an AI platform designed to combat the most critical insider risks threatening vital corporate data. Built…