Category: HelpnetSecurity
According to recent surveys, 98% of organizations keep their financial, business, customer and/or employee information in the cloud but, at…
In this Help Net Security interview, Jamieson O’Reilly, Founder of DVULN, discusses adversary simulations, shedding light on challenges rooted in…
A publicly exposed API of social media platform Spoutible may have allowed threat actors to scrape information that can be…
Cisco announced Motific, Cisco’s SaaS product that allows for trustworthy GenAI deployments in organizations. Born from Outshift, Cisco’s incubation business,…
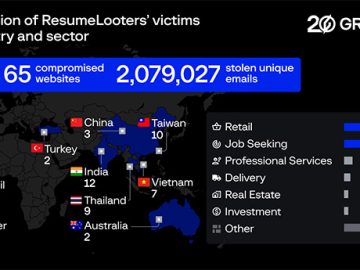
Group-IB identified a large-scale malicious campaign primarily targeting job search and retail websites of companies in the Asia-Pacific region. The…
IBM announced IBM LinuxONE 4 Express, extending the latest performance, security and AI capabilities of LinuxONE to small and medium…
Five days after Mastodon developers pushed out fixes for a remotely exploitable account takeover vulnerability (CVE-2024-23832), over 66% of Mastodon…
In this Help Net Security video, Dan Erel, VP of Security at SeeMetrics, discusses NIST Cybersecurity Framework (CSF) 2.0. NIST…
Working at the speed of digital business is a constant challenge. But in today’s increasingly automated operational environment, crypto agility—i.e.,…
In this Help Net Security interview, Marco Eggerling, Global CISO at Check Point, discusses the challenge of balancing data protection…
Our list of cybersecurity books has been curated to steer your professional growth in 2024. This selection aims to provide…
Today’s pervasive cyberattacks are forcing the majority of companies to pay ransoms and break their ‘do not pay’ policies, with…