Category: HelpnetSecurity
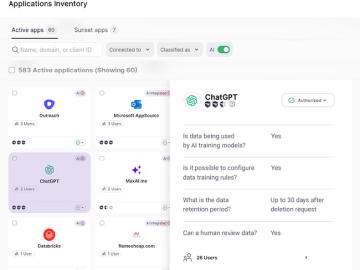
Wing Security unveils an automatic advanced approach to counter the evolving risks of Intellectual Property (IP) and data leakage into…
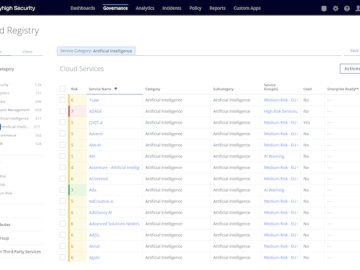
Skyhigh Security announced an AI-driven DLP Assistant as an advanced DLP capability within its Security Service Edge (SSE) portfolio. The…
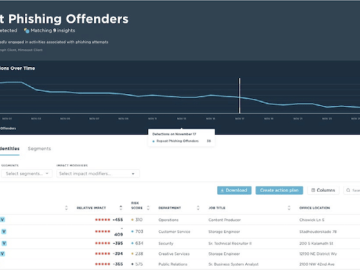
Living Security announced Unify Power Insights, which combines intelligence across multiple identity management and security tools to pinpoint visibility into…
Kaspersky’s researchers have developed a lightweight method to detect indicators of infection from sophisticated iOS spyware such as NSO Group’s…
In the new stable release of the Chrome browser, Google has fixed three security vulnerabilities affecting the V8 engine, including…
In this Help Net Security interview, Chris Mixter, Vice President, Analyst at Gartner, discusses the dynamic world of CISOs and…
Navigating layoffs is complex and difficult for many reasons. Not only do human resources and direct managers bear the onus…
Employees play a significant role in safeguarding organizational assets. With a constantly evolving threat landscape, cybersecurity awareness training is an…
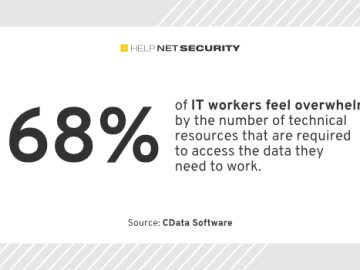
Increasing data requests overwhelm IT teams, but security concerns hinder their ability to provide employees with access to timely data,…
Atlassian has patched a critical vulnerability (CVE-2023-22527) in Confluence Data Center and Confluence Server that could lead to remote code…
Misinformation and disinformation are biggest short-term risks, while extreme weather and critical change to Earth systems are greatest long-term concern,…
As cyber threats grow more sophisticated, understanding and implementing robust cybersecurity frameworks is crucial for organizations of all sizes. This…