Category: HelpnetSecurity
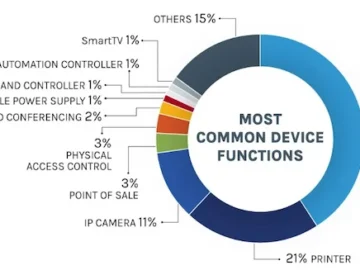
Security teams are often surprised when they discover the range and number of devices connected to their networks. The total…
Information moves across cloud platforms, personal devices, and AI tools, often faster than security teams can track it. Proofpoint’s 2025…
Ransomware remains one of the biggest operational risks for retailers, but the latest data shows a shift in how these…
PromptLock, the AI-powered proof-of-concept ransomware developed by researchers at NYU Tandon and initially mistaken for an active threat by ESET,…
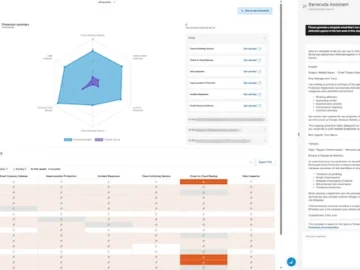
Barracuda Networks launched Barracuda Assistant, powered by Barracuda AI. Integrated into the BarracudaONE cybersecurity platform, Barracuda Assistant accelerates security operations…
On Tuesday, CISA added two vulnerabilities to its Known Exploited Vulnerabilities catalog: CVE-2025-11371, which affects Gladinet’s CentreStack and Triofox file-sharing…
A coordinated international operation has led to 18 arrests in a massive credit card fraud case worth at least €300…
In this Help Net Security interview, Dilek Çilingir, Global Forensic & Integrity Services Leader at EY, discusses how AI is…
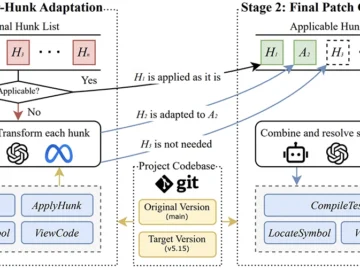
Keeping older software versions secure often means backporting patches from newer releases. It is a routine but tedious job, especially…
VulnRisk is an open-source platform for vulnerability risk assessment. It goes beyond basic CVSS scoring by adding context-aware analysis that…
Smart doorbells, connected cameras, and home monitoring systems have become common sights on doorsteps and living rooms. They promise safety…
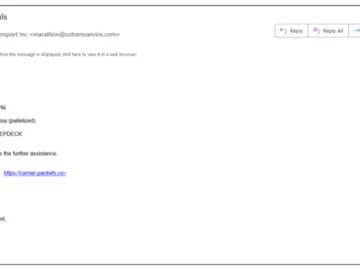
Cybercriminals are compromising logistics and trucking companies by tricking them into installing remote monitoring and management (RMM) tools, Proofpoint researchers…