Category: HelpnetSecurity
Over its journey from Windows 9x to Windows 11, Microsoft has implemented multiple security overhauls, each addressing the challenges of…
With its wealth of sensitive patient data, the healthcare industry has become a prime target for cybercriminals leveraging AI tools….
Without the right metrics, vulnerability management is pretty pointless. If you’re not measuring, how do you know it’s working? So…
Nearly 8 in 10 small business leaders admit they are anxious about the safety of their company’s sensitive data and…
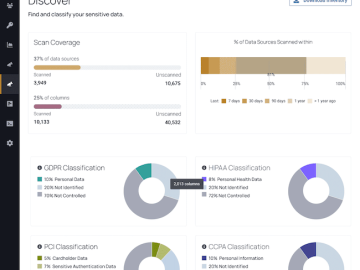
Immuta released Immuta Discover, a new product for automated tagging and classification on cloud data platforms. Immuta Discover enables data…
President Biden issued a landmark Executive Order to ensure that America leads the way in seizing the promise and managing…
CISA launched a new version of Logging Made Easy (LME), a straightforward log management solution for Windows-based devices that can…
Google has expanded its bug bounty program, aka Vulnerability Rewards Program (VRP), to cover threats that could arise from Google’s…
At some point in the movie “Groundhog Day,” Phil Connors breaks his bedside radio when he is woken up (yet…
Generative AI has emerged as a powerful tool, heralded for its potential but also scrutinized for its implications. Enterprises will…
More than one-third of companies still do not have a well-rounded, holistic ransomware strategy in place, according to Zerto. Immediate…
85% of small business leaders say they are ready to respond to a cyber incident despite a record-high 73% reporting…