Category: HelpnetSecurity
Data Theorem introduced an attack path analysis of APIs and software supply chain exploits to its cloud-native application protection platform…
Following in the footsteps of BeyondTrust and CloudFlare, 1Password has revealed that it has been affected by the Okta Support…
AI has been the shiniest thing in tech since at least November 2022, when ChatGPT was made available to the…
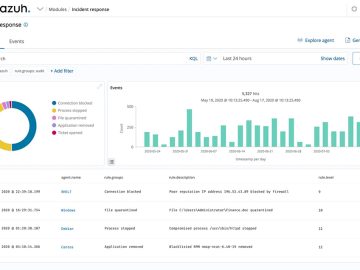
Wazuh is an open-source platform designed for threat detection, prevention, and response. It can safeguard workloads in on-premises, virtual, container,…
Security professionals want to pursue high-impact work, but they’re being held back by growing workloads, shrinking budgets, and a worsening…
45% of CIOs are beginning to work with their CxO peers to bring IT and business area staff together to…
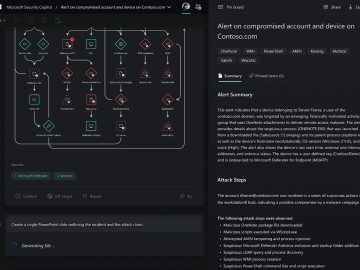
Microsoft Security Copilot has been made available to a larger number of enterprise customers, via an invitation-only Early Access Program….
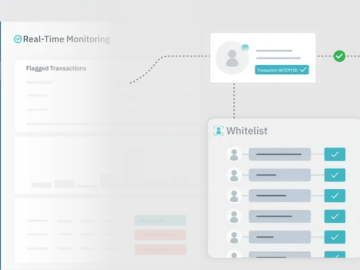
Unit21 launches Real-Time Monitoring to fight real-time fraud and transform the landscape of risk management. With Real-Time Monitoring, fraud prevention…
As passwordless identity becomes mainstream, the term “passkey” is quickly becoming a new buzzword in cybersecurity. But what exactly is…
Modern application security strategies must support and enable modern software development, even as it rapidly scales, according to Mend.io. Just…
While 93% of companies recognize the risks associated with using generative AI inside the enterprise, only 9% say they’re prepared…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: North Korean hackers are targeting…