Category: HelpnetSecurity
97% of organizations are struggling to secure their IoT and connected products to some degree, according to Keyfactor. The research…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Turning military veterans into cybersecurity…
In an era where data security is paramount, the recent revelations about firmware backdoors implanted by Chinese government-backed hackers serve…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, Flexxon, Fortanix, Fortinet, SailPoint,…
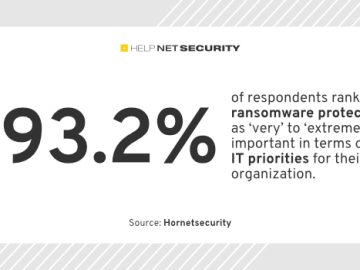
60% of companies are ‘very’ to ‘extremely’ concerned about ransomware attacks, according to latest research from Hornetsecurity. Businesses acknowledge ransomware…
Companies are losing revenue in the fight against malicious bot attacks, according to survey by Kasada. Despite spending millions of…
Check Point launched Quantum SASE, integrating technologies from newly acquired Perimeter 81. This integrated offering addresses organizations’ needs for a…
The “contain user” feature select Microsoft Defender for Endpoint customers have been trying out since November 2022 is now available…
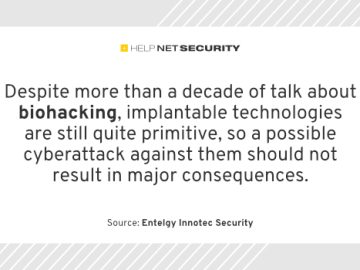
Can our bodies be hacked? The answer may be yes, in that anyone can implant a chip under the skin…
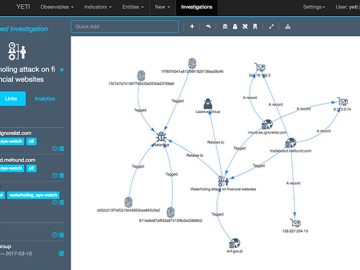
Yeti serves as a unified platform to consolidate observables, indicators of compromise, TTPs, and threat-related knowledge. It enhances observables automatically,…
Permission Slip, an iPhone and Android app developed by Consumer Reports, helps users ask companies and data brokers to stop…
Cyber insurance has been around longer than most of us think. When American International Group (AIG) launched the first cyber…