Category: HelpnetSecurity
71% of IT professionals stated that cloud-related costs make up 30% or more of their total IT spend, according to…
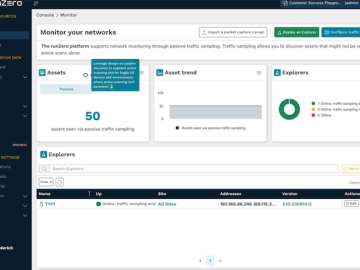
runZero has unveiled the availability of of their new runZero Platform, which introduces a number of new features, most notably…
Software development firm JetBrains has fixed a critical vulnerability (CVE-2023-42793) in its TeamCity continuous integration and continuous delivery (CI/CD) solution,…
The number of victim organizations hit by Cl0p via vulnerable MOVEit installations has surpassed 2,000, and the number of affected…
Immersive Labs unveiled the expansion of its AI-ready platform, now with coverage across the entire organization through its new Workforce…
Ransomed.vc, a relatively new ransomware / cyber extortion group, claims to have hacked Sony and made off with valuable data….
The surge in digital economic growth and our increasing dependence on it make cybersecurity a critical profession. In this Help…
Vulnerability scanners delve into systems to uncover security gaps. The primary mission? To fortify organizations against breaches and shield sensitive…
With National Coding Week behind us, the development community has had its annual moment of collective reflection and focus on…
MITRE ATT&CK, a common language for cybersecurity professionals to communicate with each other and better understand real-world adversary behaviors, celebrates…
While many IT workers see the productivity benefits of AI, 56% believe it benefits employers more than employees, according to…
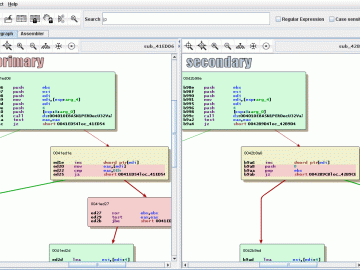
BinDiff is a binary file comparison tool to find differences and similarities in disassembled code quickly. It was made open…