Category: HelpnetSecurity
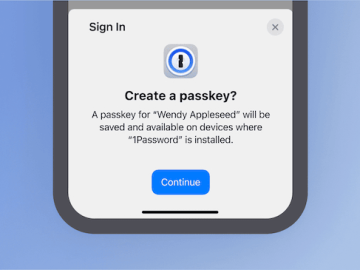
1Password customers can now create, manage, and sign in with passkeys on a growing number of websites and apps, providing…
Enterprises that leverage observability increase operational efficiency and grow revenue, according to SolarWinds. The report explores how enterprises can act…
All enterprise organizations are, in essence, software publishers, regardless of their industry. This is because every enterprise relies on custom…
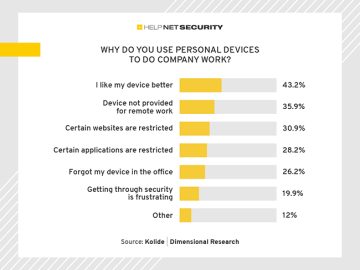
3 out of 4 workers use personal (and often unmanaged) phones and laptops for work and nearly half of companies…
Far exceeding a traditional public cloud platform, Azure is a comprehensive suite of over 200 products and cloud services engineered…
60% of cyberattacks against the industrial sector are led by state-affiliated actors and often unintentionally enabled by internal personnel (about…
72% of banks and credit unions are prioritizing compliance when evaluating fintechs, citing it as their top criteria in the…
Data breaches are a dime a dozen. Although it’s easy to look at that statement negatively, the positive viewpoint is…
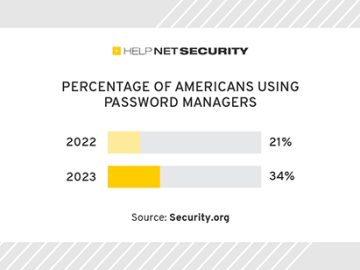
One in three Americans now use password managers, up from one in five in 2022, according to an online poll…
In this Help Net Security interview, Scott Sutherland, VP of Research at NetSPI, delves into the intricacies of their Breach…
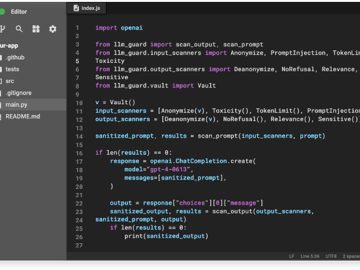
LLM Guard is a toolkit designed to fortify the security of Large Language Models (LLMs). It is designed for easy…
Energized by the hype around generative AI, enterprises are aggressively pursuing practical applications of this new technology while remaining cautious…