Category: HelpnetSecurity
Over 70% of CISOs feel that the importance of information security is not recognised by senior leadership, according to BSS….
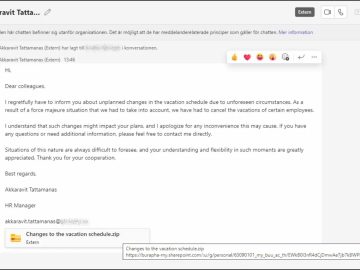
A new phishing campaign taking advantage of an easily exploitable issue in Microsoft Teams to deliver malware has been flagged…
SecuX revealed its latest creation, the Shield BIO card-type hardware wallet. The Shield BIO combines biometric fingerprint authentication with the…
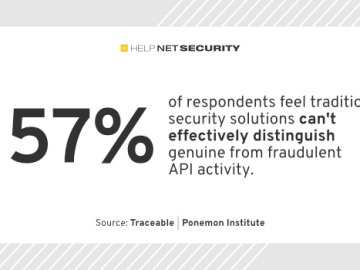
While APIs are essential to many operations and used extensively, a lack of prioritization and understanding is leading us towards…
73% of board members believe they face the risk of a major cyber attack in the next 12 months, a…
In this Help Net Security interview, Adrien Petit, CEO at Uncovery, discusses the benefits that organizations can derive from implementing…
Sending an email with a forged address is easier than previously thought, due to flaws in the process that allows…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: The misconceptions preventing wider adoption…
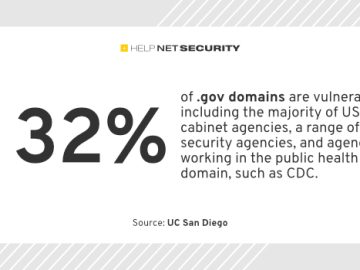
Apple has patched two zero-day vulnerabilities (CVE-2023-41064, CVE-2023-41061) exploited to deliver NSO Group’s Pegasus spyware. “The exploit chain was capable…
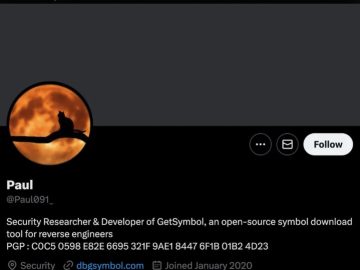
North Korean threat actors are once again attempting to compromise security researchers’ machines by employing a zero-day exploit. The warning…
Here’s a look at the most interesting products from the past week, featuring releases from CyberSaint, Ghost Security, Hornetsecurity, NTT…
Microsoft addressed 33 CVEs in Windows 10 and 11 last month after nearly 3x that number in July. But despite…