Category: HelpnetSecurity
Hornetsecurity has launched its Plan 4 “Compliance & Awareness” solution of 365 Total Protection Suite, offering a higher level of…
The LockBit ransomware group has breached Zaun, a UK-based manufacturer of fencing systems for military sites and critical utilities, by…
In this Help Net Security interview, Thorsten Hau, CEO at fidentity, discusses the legal validity of qualified digital signatures, demonstrating…
Original equipment suppliers (OEMs) and their suppliers who are weighing how to invest their budgets might be inclined to slow…
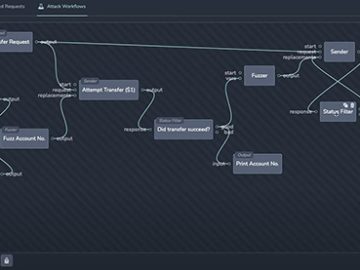
Reaper is an open-source reconnaissance and attack proxy, built to be a modern, lightweight, and efficient equivalent to Burp Suite/ZAP….
Cybersecurity is not just a career field on the rise – it’s a calling that’s increasingly vital to the infrastructure…
Here’s a look at the most interesting products from the past month, featuring releases from: Action1, Adaptive Shield, Bitdefender, Bitwarden,…
65% of organizations confirmed that ransomware is one of the top three threats to their viability, and for 13%, it…
Blockchain technology has gained significant traction due to its decentralized nature and immutability, providing transparency and security for various applications,…
85% of phishing emails utilized malicious links in the content of the email, and spam emails increased by 30% from…
Losses from global roaming fraud are anticipated to exceed $8 billion by 2028; driven by the increase in bilateral roaming…
Nidhi Gani is a seasoned regulatory affairs professional with over a decade of experience in cybersecurity, medical devices, and digital…