Category: HelpnetSecurity
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Adapting authentication to a cloud-centric…
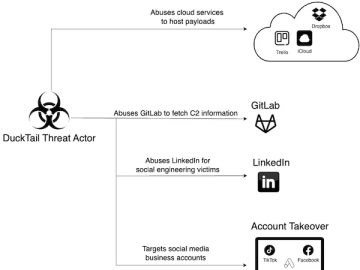
Quite some money can be made from selling compromised business and ad accounts on social media platforms, and the Ducktail…
Adversary-sponsored research contests on cybercriminal forums focus on new methods of attack and evasion, according to Sophos. The contests mirror…
Here’s a look at the most interesting products from the past week, featuring releases from Ciphertex Data Security, ComplyCube, Fortinet,…
A significant gap is emerging between insurance providers, as organizations skip the fine print and seek affordable and comprehensive coverage,…
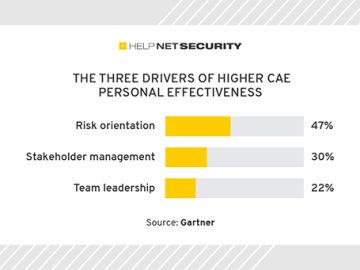
Chief audit executives (CAEs) have identified risk orientation, stakeholder management, and team leadership as the top three characteristics of the…
Since March 2023 (and possibly even earlier), affiliates of the Akira and LockBit ransomware operators have been breaching organizations via…
ESET researchers have identified two active campaigns targeting Android users, where the threat actors behind the tools for Telegram and…
The number of IoT devices in enterprise networks and across the internet is projected to reach 29 billion by the…
In this Help Net Security interview, Kevin Valk, co-CEO at Codean, discusses the consequences of relying solely on automated tools…
69% of top-performing CISOs dedicate recurring time on their calendars for personal professional development, according to Gartner. This is compared…
ComplyCube enhanced its Document Checks solution with automated Field Redaction capabilities. This feature systematically masks sensitive Personal Identifiable Information (PII)…