Category: HelpnetSecurity
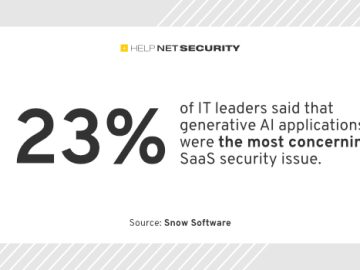
IT leaders are grappling with anxiety over the risks of generative AI despite continued confidence in their software-as-a-service (SaaS) security…
Financial and risk advisory firm Kroll has suffered a SIM-swapping attack that allowed a threat actor to access files containing…
Researchers have released additional details about the recently patched four vulnerabilities affecting Juniper Networks’ SRX firewalls and EX switches that…
In the era of data-driven decision making, businesses are harnessing the power of machine learning (ML) to unlock valuable insights,…
In this Help Net Security interview, Florian Forster, CEO at Zitadel, discusses the challenges CISOs face in managing authentication across…
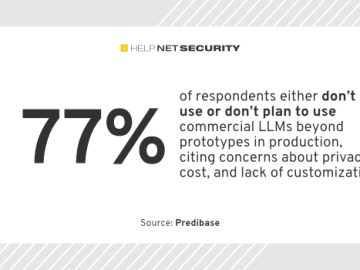
The expansion of large language models (LLMs) in recent times has brought about a revolutionary change in machine learning processes…
Cloud Native Application Protection Platforms (CNAPPs) have emerged as a critical category of security tooling in recent years due to…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Network detection and response in…
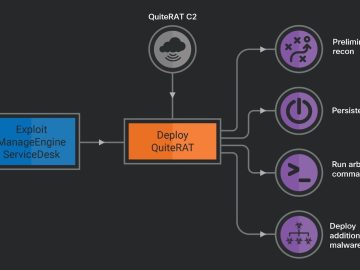
North Korean state-sponsored hackers Lazarus Group have been exploiting a ManageEngine ServiceDesk vulnerability (CVE-2022-47966) to target internet backbone infrastructure and…
Median attacker dwell time—the time from when an attack starts to when it’s detected—shrunk from 10 to eight days for…
Here’s a look at the most interesting products from the past week, featuring releases from Security Onion, OffSec, ImmuniWeb, LOKKER,…
Cybersecurity insurance is a rapidly growing market, swelling from approximately $13B in 2022 to an estimated $84B in 2030 (26%…