Category: HelpnetSecurity
Here’s a look at the most interesting products from the past week, featuring releases from Security Onion, OffSec, ImmuniWeb, LOKKER,…
Cybersecurity insurance is a rapidly growing market, swelling from approximately $13B in 2022 to an estimated $84B in 2030 (26%…
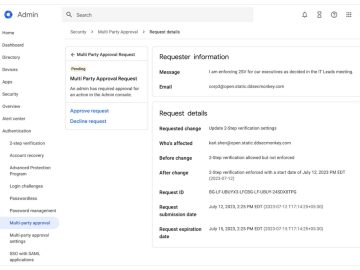
New capabilities in Google Workspace will help enterprises improve account and data security, by making unauthorized takeover of admin and…
In this Help Net Security interview, Jonathan Segev, IEEE 802.11 Task Group (TG) Chair of next-generation positioning (TGaz) at IEEE,…
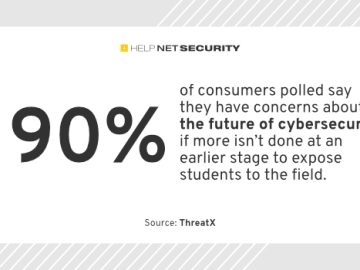
Consumers believe today’s cybersecurity talent shortage is in large part due to limited exposure to the profession and a lack…
Kingston Digital Europe has launched the Kingston IronKey Keypad 200C, a hardware-encrypted USB Type-C drive that ensures both security and…
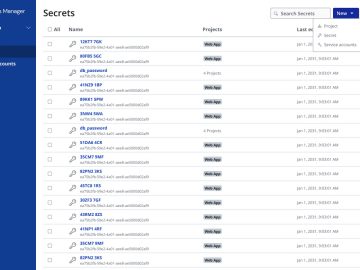
Bitwarden, a popular open-source password management service, has released Bitwarden Secrets Manager, an open-source, end-to-end encrypted solution that helps development,…
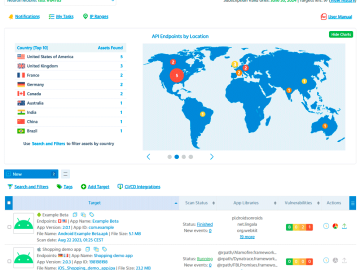
ImmuniWeb has introduced ImmuniWeb Neuron Mobile – its 6th product available on the ImmuniWeb AI Platform that currently covers over…
Offensive Security has released Kali Linux 2023.3, the latest version of its penetration testing and digital forensics platform. New tools…
As security vulnerabilities are reported to you time and again, you may ask yourself: “Why don’t these developers learn the…
In this Help Net Security interview, Gerwin van der Lugt, CTO at Oddity, discusses the future of surveillance and AI’s…
Fragmented access policies are top security concern in multi-cloud environments, with more than 75% of enterprises reporting they do not…