Category: HelpnetSecurity
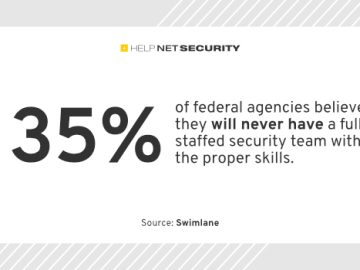
Federal agencies are prepared to meet the zero trust executive order requirements from the Biden Administration with just over a…
A phishing campaign using QR codes has been detected targeting various industries, with the aim to acquire Microsoft credentials. “The…
Ecommerce platforms are incorporating sophisticated fraud detection measures, but fraudsters, too, are refining their strategies. In this Help Net Security…
A quarter of IT professionals are seriously contemplating leaving their current jobs within the next six months, potentially costing US…
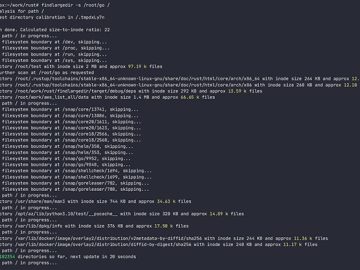
Findlargedir is a tool written to help quickly identify “black hole” directories on any filesystem having more than 100k entries…
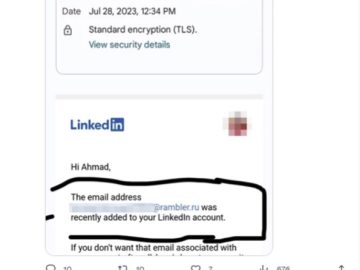
LinkedIn users are being targeted in an ongoing account hijacking campaign, are getting locked out of their accounts; the hacked…
Administrators of Citrix NetScaler ADC and Gateway appliances should check for evidence of installed webshells even if they implemented fixes…
Two stack-based buffer overflow bugs (collectively designated as CVE-2023-32560) have been discovered in Ivanti Avalanche, an enterprise mobility management solution….
Representatives from Amazon, Anthropic, Google, Inflection, Meta, Microsoft, and OpenAI recently convened at the White House for a meeting with…
The role of the CISO has evolved into a critical position that encompasses many responsibilities aimed at safeguarding digital assets,…
Last week, on August 1-2, 2023, Cybertech arrived at the Kigali Convention Center in Kigali, Rwanda, in partnership with the…
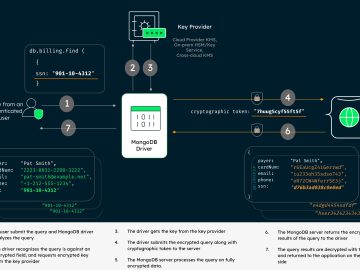
MongoDB Queryable Encryption helps organizations protect sensitive data when it is queried and in-use on MongoDB. It reduces the risk…