Category: HelpnetSecurity
Regulatory compliance and cybersecurity improvement are not two sides of the same coin: they are distinct pillars that demand specialized…
As AI technology advances, it is essential to remain mindful of familiar and emerging risks. Education is critical to fostering…
An overwhelming number of respondents familiar with ChatGPT were concerned about the risks it poses to security and safety, according…
Computer scientists at the University of Waterloo have discovered a method of attack that can successfully bypass voice authentication security…
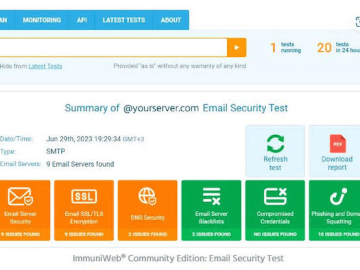
Running about 200,000 daily security scans, the free Community Edition now has an online security test to quickly verify security,…
As 40% of consumers harbor skepticism regarding organizations’ data protection capabilities, 75% would shift to alternate companies following a ransomware…
Small organizations face the same security threats as organizations overall but have less resources to address them, according to Netwrix….
In this Help Net Security interview, Mike Fey, CEO of Island, explains the differences between consumer browsers and the Island…
IT leaders are losing sleep over improving overall IT performance (60%), data security (50%), process risk and compliance (46%), and…
Aggregated honeypot data, over a six-month period, showed that more than 50% of the attacks focused on defense evasion, according…
Enterprise leaders in procurement, IT, and finance need to take immediate action to rationalize their SaaS portfolios to prevent spending…
Here’s a look at the most interesting products from the past month, featuring releases from: 1Password, Bitdefender, Cequence Security, ConnectSecure,…