Category: HelpnetSecurity
Security teams are stretched, with not enough people, skills or budget to cope with all their priorities, according to Panaseer….
Island announced an enterprise-grade set of Data Loss Prevention (DLP) capabilities for all popular interactive AI-type applications including ChatGPT, Bard…
The importance of software bills of materials (SBOMs) has grown substantially in recent years as organizations recognize the need for…
Infosecurity Europe is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. The…
Compromised credentials were found within the logs of info-stealing malware traded on illicit dark web marketplaces over the past year,…
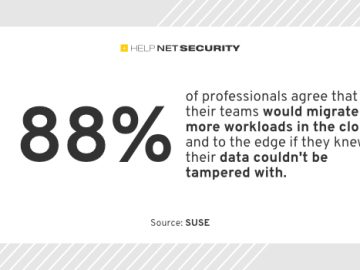
The growing adoption of cloud has elevated cloud security fear for IT teams, as they grapple with the challenges and…
In this Help Net Security interview, Sunil Potti, VP and GM, Cloud Security Google Cloud, talks about how new security…
IT teams have made security efforts and progress in zero-trust implementation strategies to establish a new sense of normalcy following…
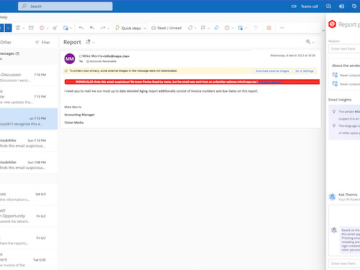
IRONSCALES announced the Beta launch of Themis Co-pilot for Microsoft Outlook, a GPT-powered chat assistant for self-service threat reporting. Powering…
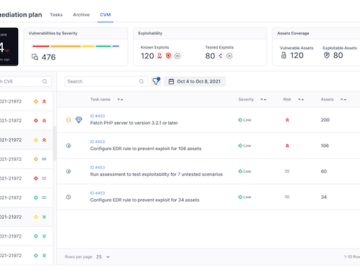
Cymulate released a new solution for organizations to run an informed continuous threat exposure management (CTEM) program. The CTEM program,…
Infosecurity Europe is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. Here’s…
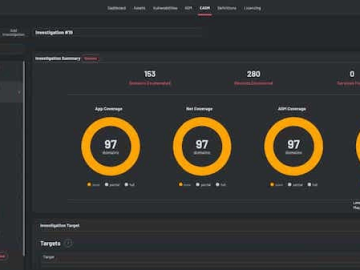
Edgescan released its new External Attack Surface Management solution, offering visibility and continuous monitoring to help secure organizations of all…