Category: HelpnetSecurity
Fraudsters are underestimating the power of AI to detect fake IDs, according to a new report from Ondato. Based on…
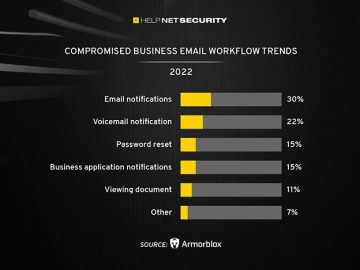
Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Making risk-based decisions in a…
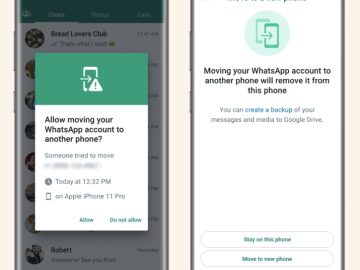
WhatsApp will be rolling out three new security features in the coming months, to provide users with increased privacy and…
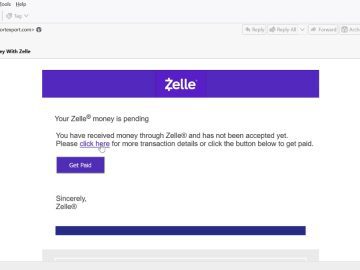
Cybercriminals have been leveraging social engineering techniques to impersonate the popular US-based digital payments network Zelle and steal money from…
Here’s a look at the most interesting products from the past week, featuring releases from BigID, Binarly, Cynalytica, GitGuardian, Netskope,…
On average, organizations store 61% of their sensitive data in the cloud, and most have experienced at least one cybersecurity…
How are data teams conquering the complexity of the modern data stack? Unravel Data has asked 350+ data scientists, engineers,…
Google has announced the Google Cloud Assured Open Source Software (Assured OSS) service, which aims to be a trusted source…
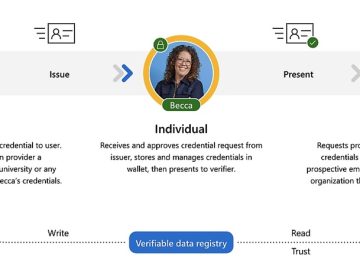
To combat the surge of fake LinkedIn accounts in recent years, Microsoft has introduced Entra Verified ID, a new feature…
It used to be that people were the greatest cybersecurity vulnerability, but this is no longer true. The rise of…
Wazuh launched Wazuh 4.4, the latest version of its open source security platform. The latest version adds multiple new features,…