Category: HelpnetSecurity
The rapid pace of cloud transformation and democratization of data has created a new innovation attack surface, leading to 3…
Five days have passed since the supply chain attack targeting 3CX customers gained wider public attention, but the software’s manufacturer…
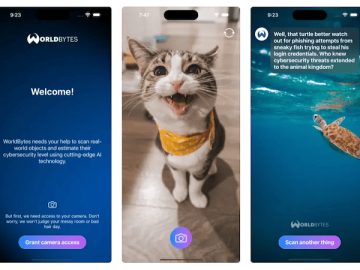
Malwarebytes launched WorldBytes, a next-generation mobile security application that takes the malware scanning technologies that customers know and love and…
US-based data storage company Western Digital has announced that it has suffered a network security incident that resulted in an…
We’ve been developing machine learning-based cybersecurity systems for many years and began developing automation for analysis in our labs in…
Locating and identifying sensitive data, including defense-in-depth strategies where a series of mechanisms are layered to protect valuable information, should…
Liran Haimovitch, CTO and co-founder of Rookout, with his extensive background in cybersecurity within the Israeli government, has a unique…
In this Help Net Security interview, Kevin Muller, CEO at Passbolt, delves into the critical concerns linked to password usage,…
Although KEV catalog vulnerabilities are frequent targets of APT Groups, a large and exploitable attack surface remains due to software…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Visa fraud expert outlines the…
OSC&R (Open Software Supply Chain Attack Reference) is an open framework for understanding and evaluating software supply chain security threats….
Only 9% of organizations are taking an agile, holistic and mature approach to securing identities throughout their hybrid and multi-cloud…