Category: HelpnetSecurity
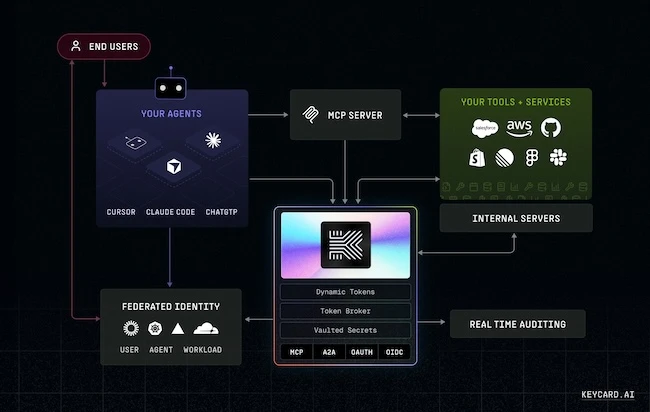
Keycard emerged from stealth with its identity and access platform for AI agents that integrates with organizations’ existing user identity…
The rapid technological advances of recent decades have transformed nearly every aspect of our lives. One major shift is that…
Blind and low-vision users face the same password challenges as everyone else, but the tools meant to make security easier…
OpenFGA is an open-source, high-performance, and flexible authorization engine inspired by Google’s Zanzibar system for relationship-based access control. It helps…
51% of European IT and cybersecurity professionals said they expect AI-driven cyber threats and deepfakes to keep them up at…
Security teams spend much of their day pulling data from reports, forums, and feeds, trying to connect clues across multiple…
Dataminr has announced its intent to acquire ThreatConnect in a transaction valuing the company at $290 million. The fusion of…
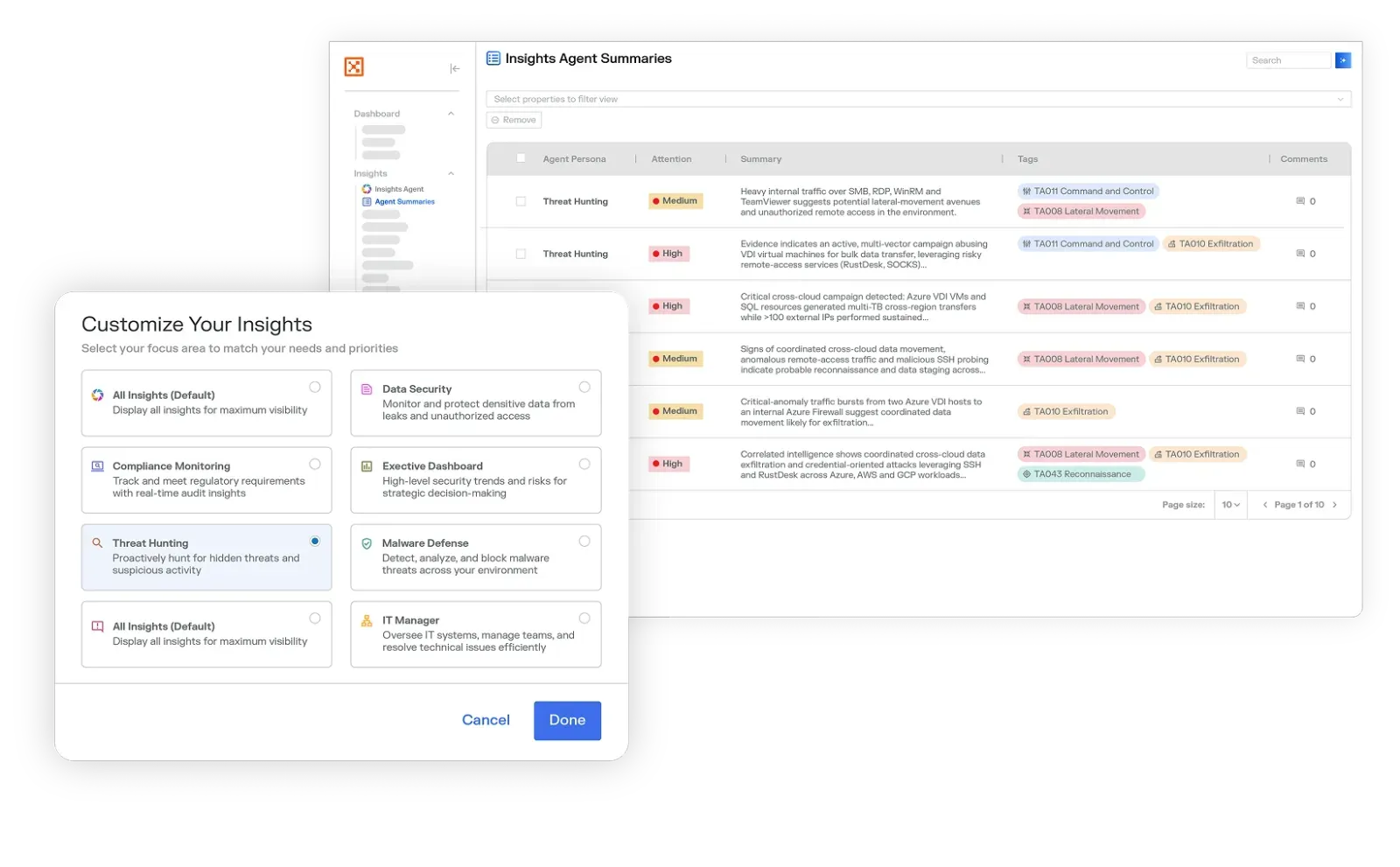
Illumio has released Insights Agent, a new capability within Illumio Insights, the company’s AI-driven cloud detection and response (CDR) solution….
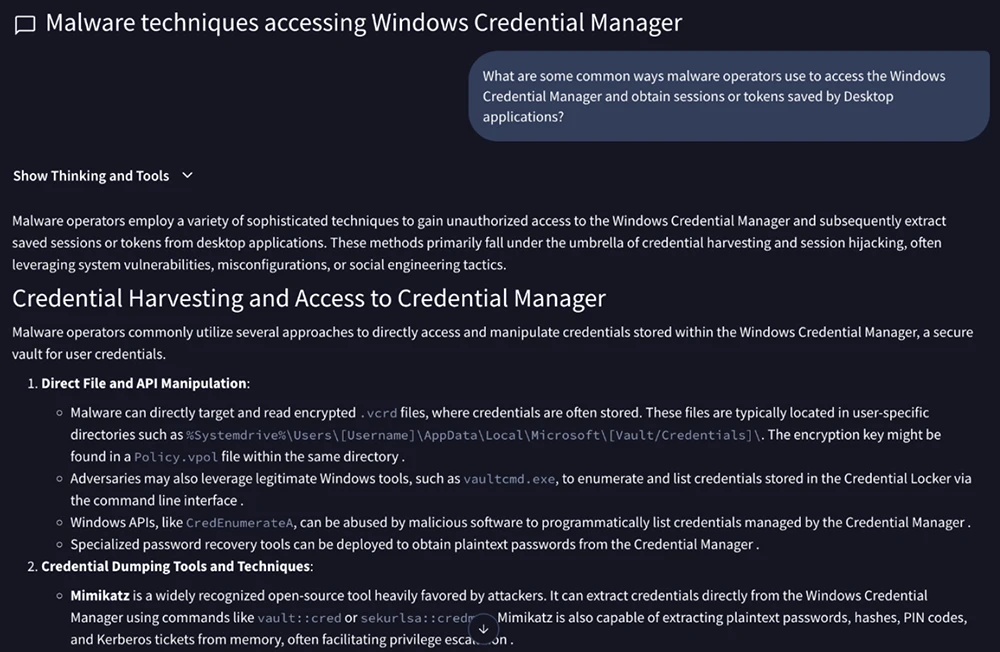
CVE-2025-33073, a Windows SMB Client vulnerability that Microsoft fixed in June 2025, is being exploited by attackers. The confirmation comes…
The official website for Xubuntu, a community-maintained “flavour” of Ubuntu that ships with the Xfce desktop environment, has been compromised…
CISO Open-Xchange | Germany | Remote – View job details As a CISO, you will lead the development and implementation…
As artificial intelligence (AI) solutions continue to evolve, the rise of agentic AI—intelligent systems that can act autonomously on behalf…