Category: HelpnetSecurity
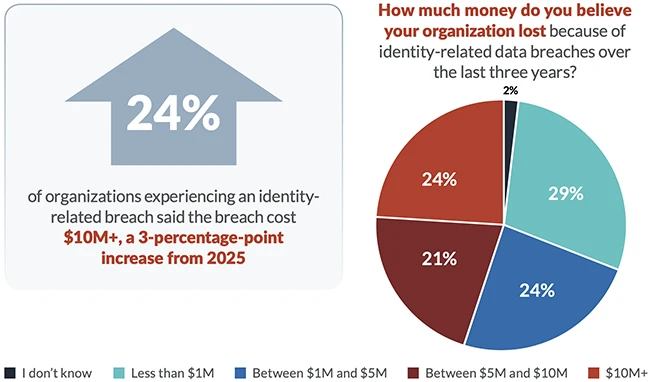
Experts across industries say they are still losing ground against identity-related breaches, even after years of investment in stronger access…
On top of several new free tools launched during the summer, ImmuniWeb released over 500 updates, improvements, new features, and…
US tech company F5 has suffered a breach, and the attackers made off with source code of and vulnerability information…
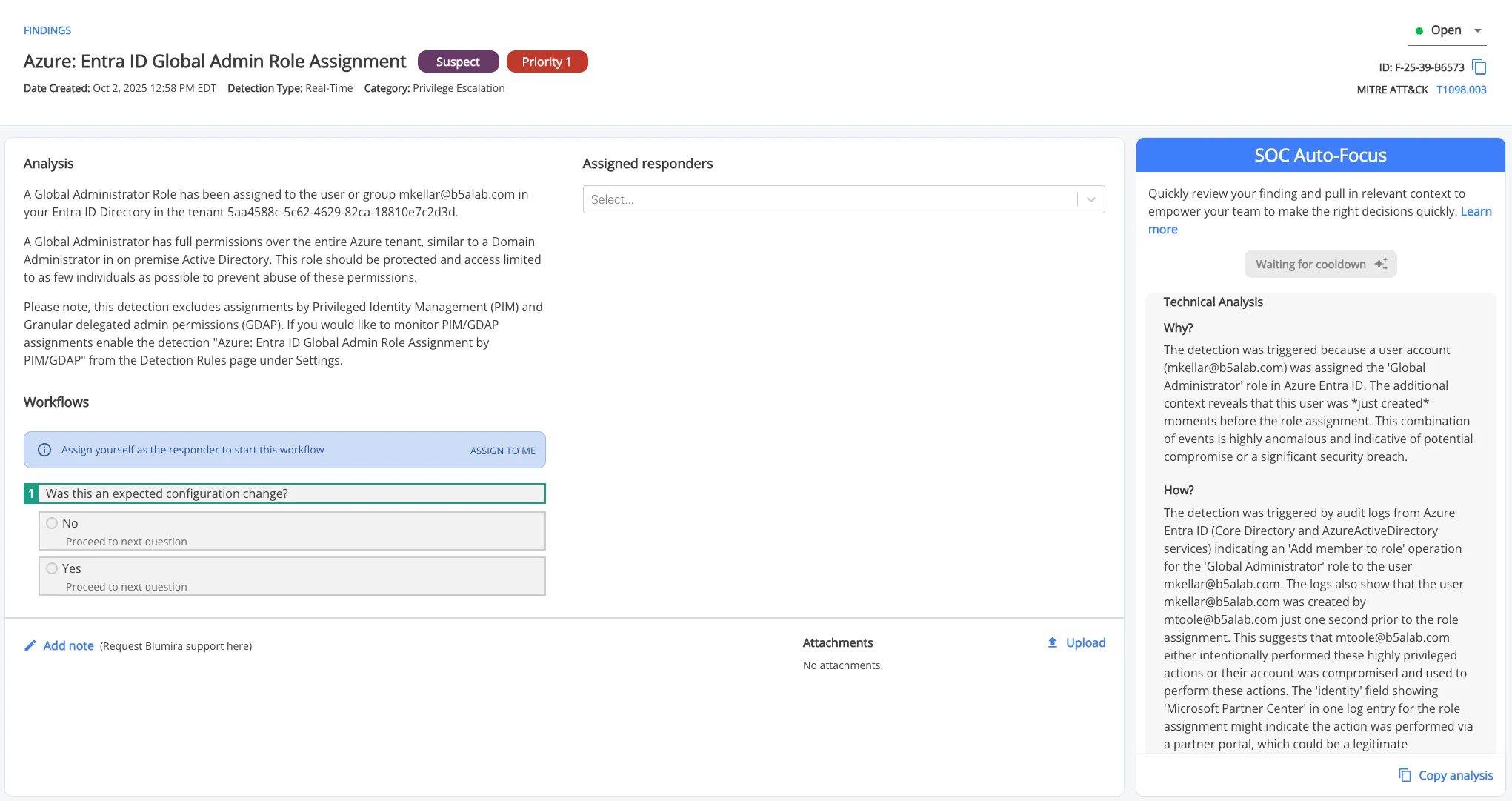
Blumira launched SOC Auto-Focus, an AI-powered security investigation tool, alongside enhancements to its Managed Service Provider (MSP) partner program. SOC…
On October 2025 Patch Tuesday, Microsoft released fixes for 175+ vulnerabilities, including three zero-days under active attack: CVE-2025-24990, CVE-2025-59230, and…
The U.S. government has seized about $15 billion worth of Bitcoin connected to what prosecutors call one of the largest…
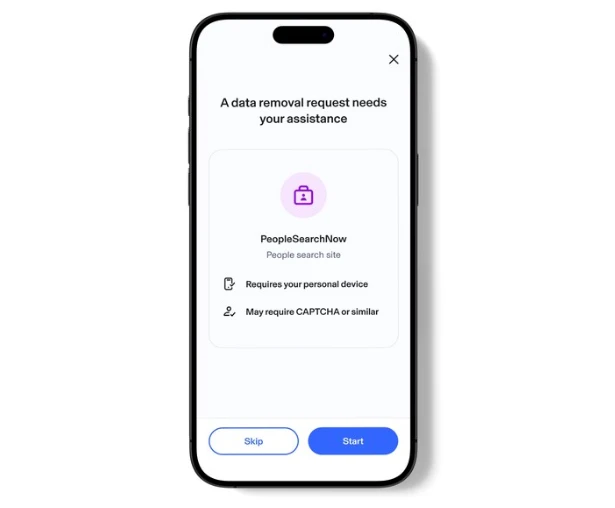
Aura new tools to help consumers reclaim control over their personal information online. The new capabilities automate some of the…
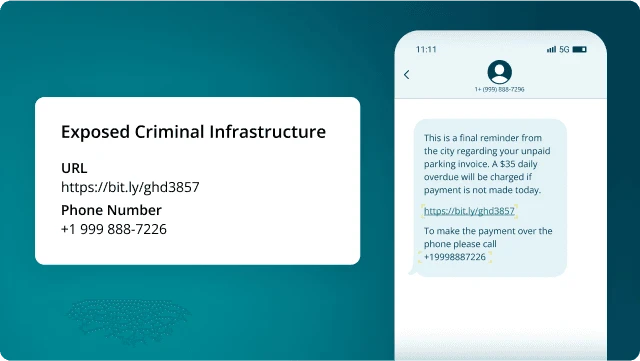
Netcraft unveiled a new solution to help protect organizations’ customers from scam texts and phone calls that impersonate their brand….
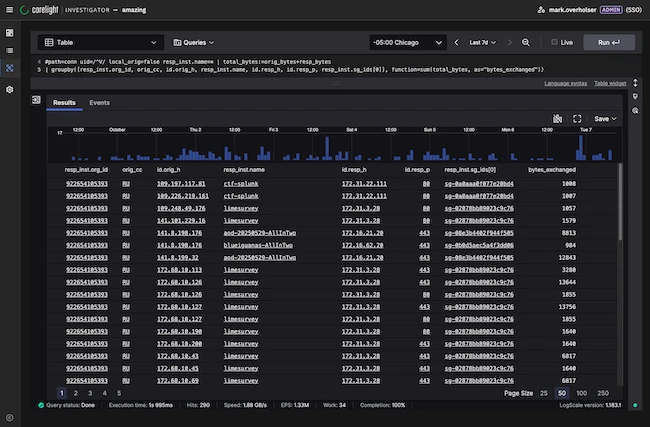
Corelight launched Flow Monitoring for AWS environments, expanding network visibility across cloud and on-premises ecosystems through comprehensive analysis of flow…
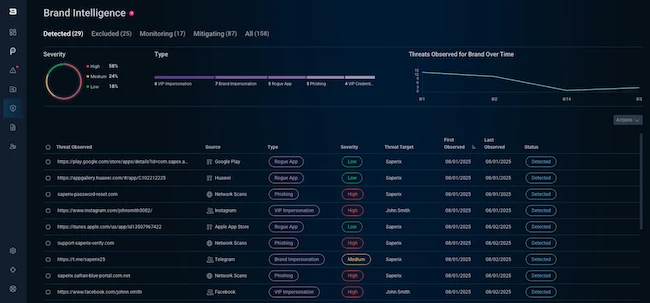
Bitsight released Bitsight Brand Intelligence, a new module in its cyber threat intelligence application, to empower security and risk teams…
Cybersecurity teams often struggle to test defenses for industrial control systems without risking disruption. A group of researchers from Curtin…
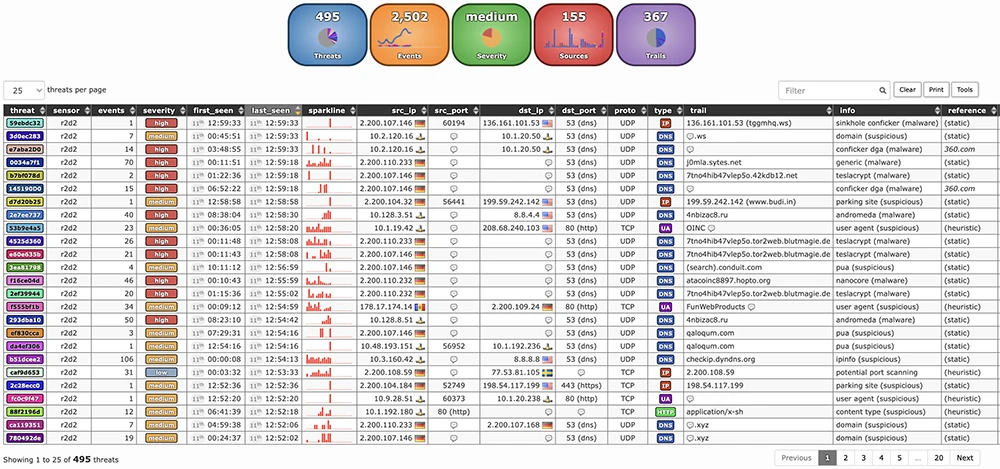
Maltrail is an open-source network traffic detection system designed to spot malicious or suspicious activity. It works by checking traffic…