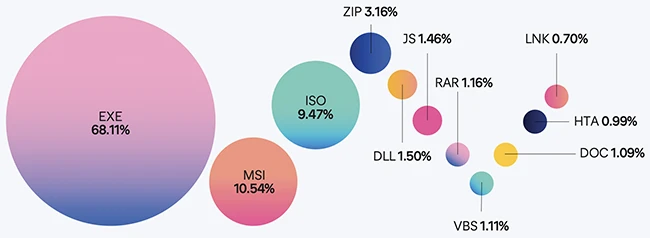
Category: HelpnetSecurity
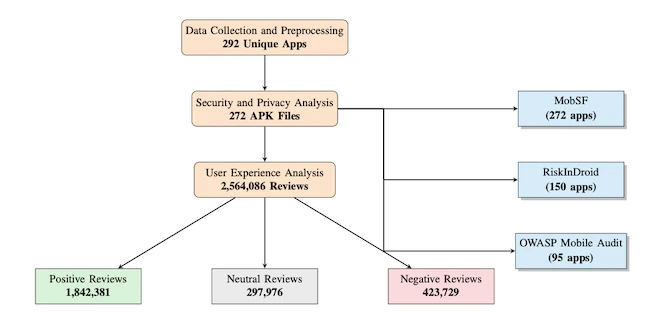
Sensitive data is moving through Android healthcare apps without adequate protection. Researchers found that many transmit information without encryption, store…
Critical infrastructure is getting older, and the cost of that decay is starting to show. The Arthur D. Little Built…
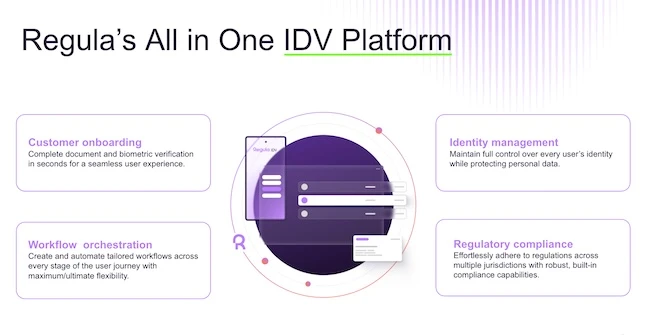
Regula has launched its Regula IDV Platform. This ready-to-use orchestration solution is designed to replace fragmented identity verification and management…
The EU’s proposed Chat Control (CSAM Regulation) aims to combat child sexual abuse material by requiring digital platforms to detect,…
A new academic study proposes a way to design privacy mechanisms that can make use of prior knowledge about how…
Solar isn’t low risk anymore. Adoption has turned inverters, aggregators, and control software into attack surfaces capable of disrupting service…
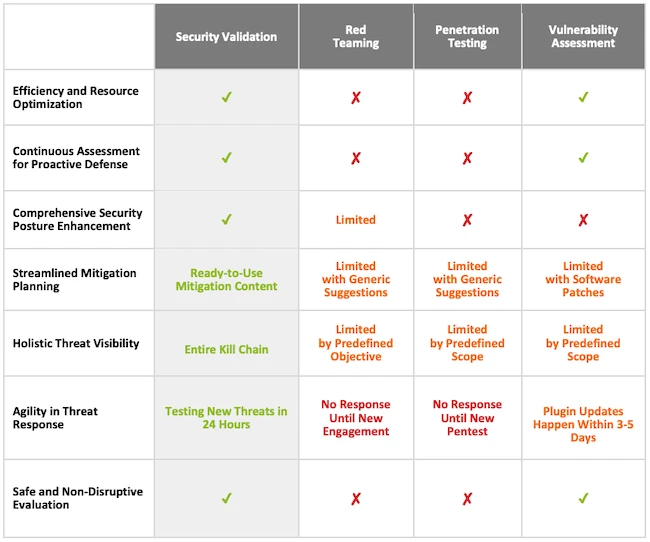
Every sizable organization invests heavily in firewalls, SIEMs, EDRs, and countless other technologies that form the backbone of a modern…
Cyber Security Analyst I First Citizens Bank | USA | Remote – View job details As a Cyber Security Analyst,…
In this Help Net Security interview, Wayman Cummings, CISO at Ochsner Health, talks about building a healthcare cybersecurity strategy, even…
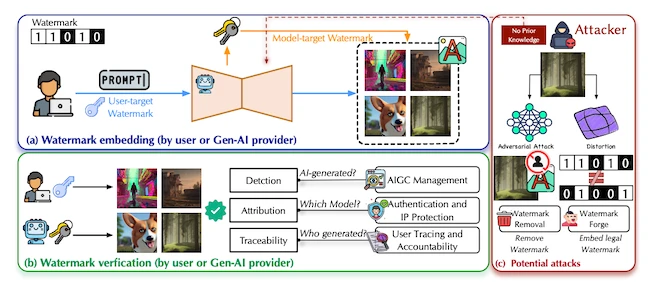
GenAI simplifies image creation, yet it creates hard problems around intellectual property, authenticity, and accountability. Researchers at Queen’s University in…
Cyber attacks are happening faster than ever. Intrusions that once took weeks or months now unfold in minutes, leaving little…
93% of U.S. healthcare organizations experienced at least one cyberattack in the past year, with an average of 43 incidents…