Category: HelpnetSecurity
Object First unveiled Ootbi Mini, a new compact immutable storage appliance designed for remote and branch offices, edge environments, and…
The cryptocurrency sector faces an existential threat on two fronts: none of the 2,138 web applications and 146 mobile apps…
Scam websites tied to online shopping, pet sales, and other e-commerce schemes continue to cause millions in losses each year….
In this Help Net Security interview, Jess Vachon, CISO at PRA Group, discusses the company’s multi-layered defense against fraud and…
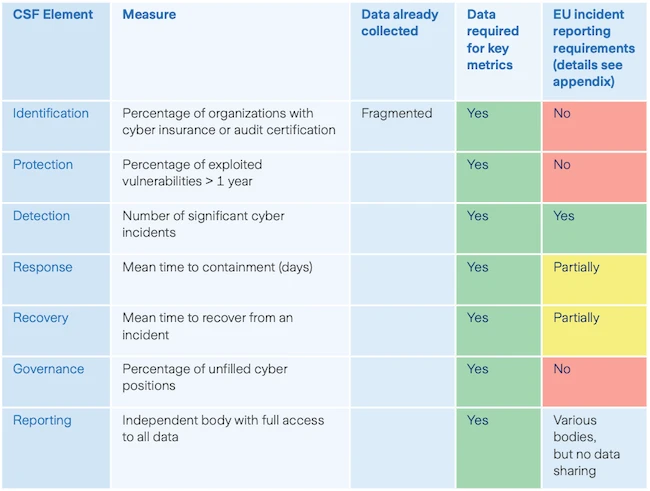
Most countries are still making national cyber policy decisions without reliable numbers. Regulations often focus on incident reporting after damage…
Varonis Systems announced the availability of Varonis Interceptor, a new approach to email security that uses multi-layered AI to detect…
North Korean hackers have stolen more than $2 billion in cryptocurrency in 2025, according to blockchain analytics firm Elliptic, and…
Palo Alto Networks researchers have discovered and analyzed “IUAM ClickFix Generator”, a phishing kit that allows less skilled attackers to…
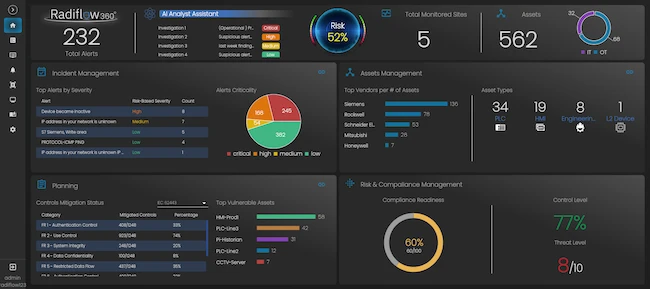
Radiflow has launched the new Radiflow360, a unified, AI-enhanced OT cybersecurity platform that delivers visibility, risk management and streamlined incident…
If you think managing cloud security is complex, try doing it across hundreds of satellites orbiting the planet. Each one…
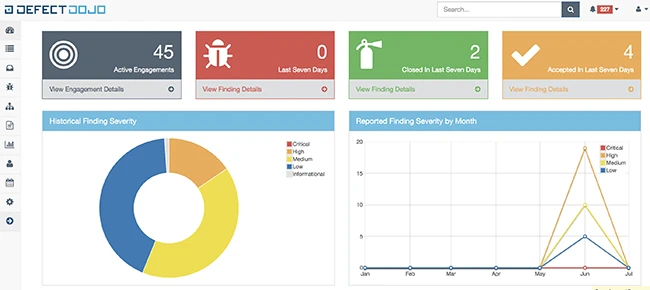
DefectDojo is an open-source tool for DevSecOps, application security posture management (ASPM), and vulnerability management. It helps teams manage security…
Cybercrime is a global problem, but not every country is equally equipped to fight it. In many developing economies, cybersecurity…