Category: HelpnetSecurity
When disaster strikes, communication often fails. Cell towers can go offline, internet connections can disappear, and people are left without…
Redis, the company behind the widely used in-memory data structure store of the same name, has released patches for a…
OPSWAT launched MetaDefender Drive with Smart Touch, a portable cybersecurity device designed for malware and compliance scanning of transient cyber…
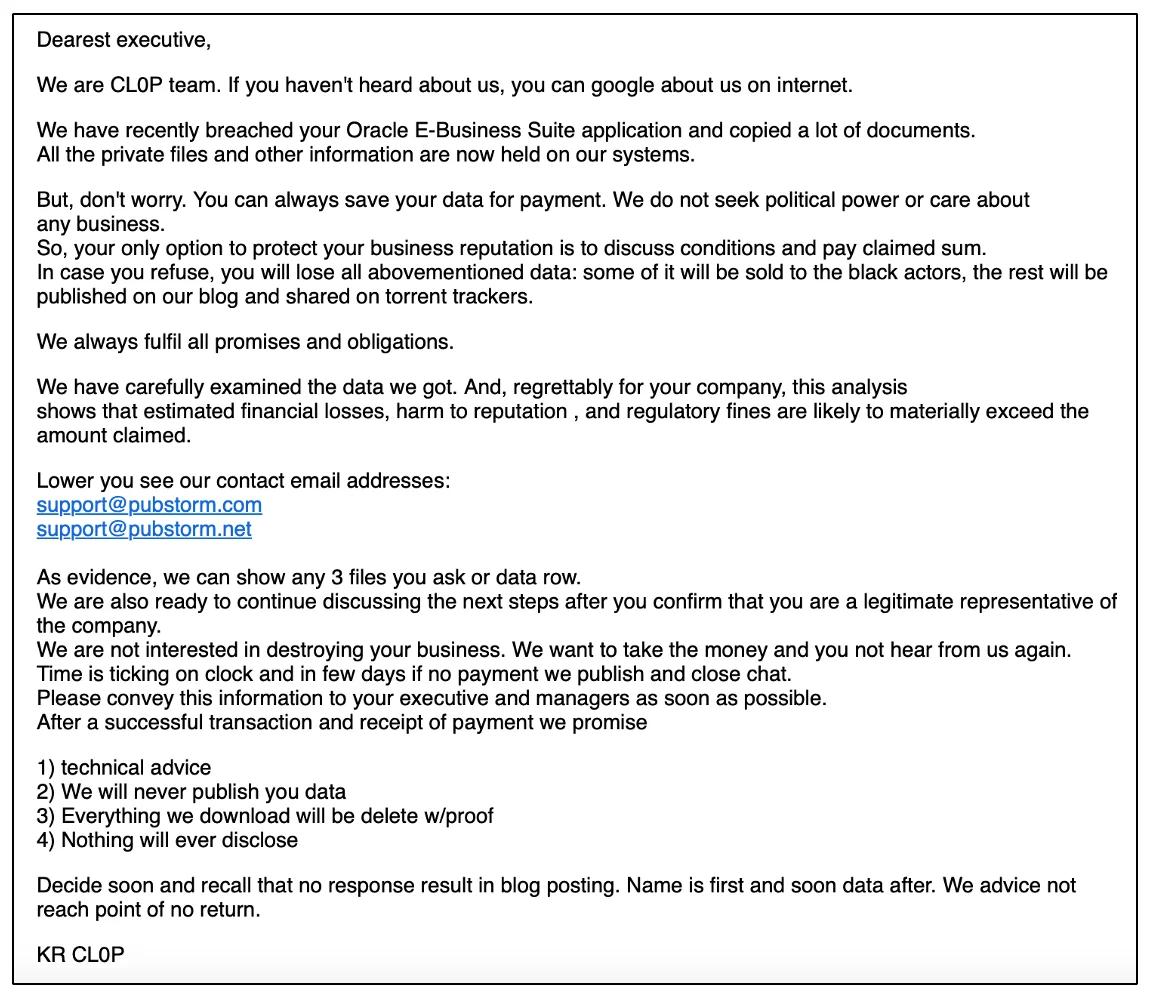
Resecurity and watchTowr researchers have analyzed the leaked scripts used by attackers to exploit CVE-2025-61882 on internet-facing Oracle ESB instances….
Application Security / DevSecOps Engineer AvetixCyber | USA | Remote – View job details As an Application Security / DevSecOps…
The wrong bug bounty strategy can flood your team with low-value reports. The right one can surface critical vulnerabilities that…
Bot farms have moved into the center of information warfare, using automated accounts to manipulate public opinion, influence elections, and…
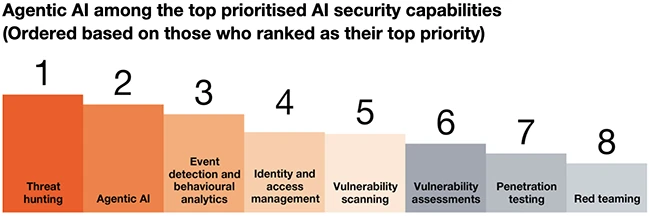
Geopolitics, emerging technology, and skills shortages are reshaping cybersecurity priorities across industries, according to a new PwC report. The findings…
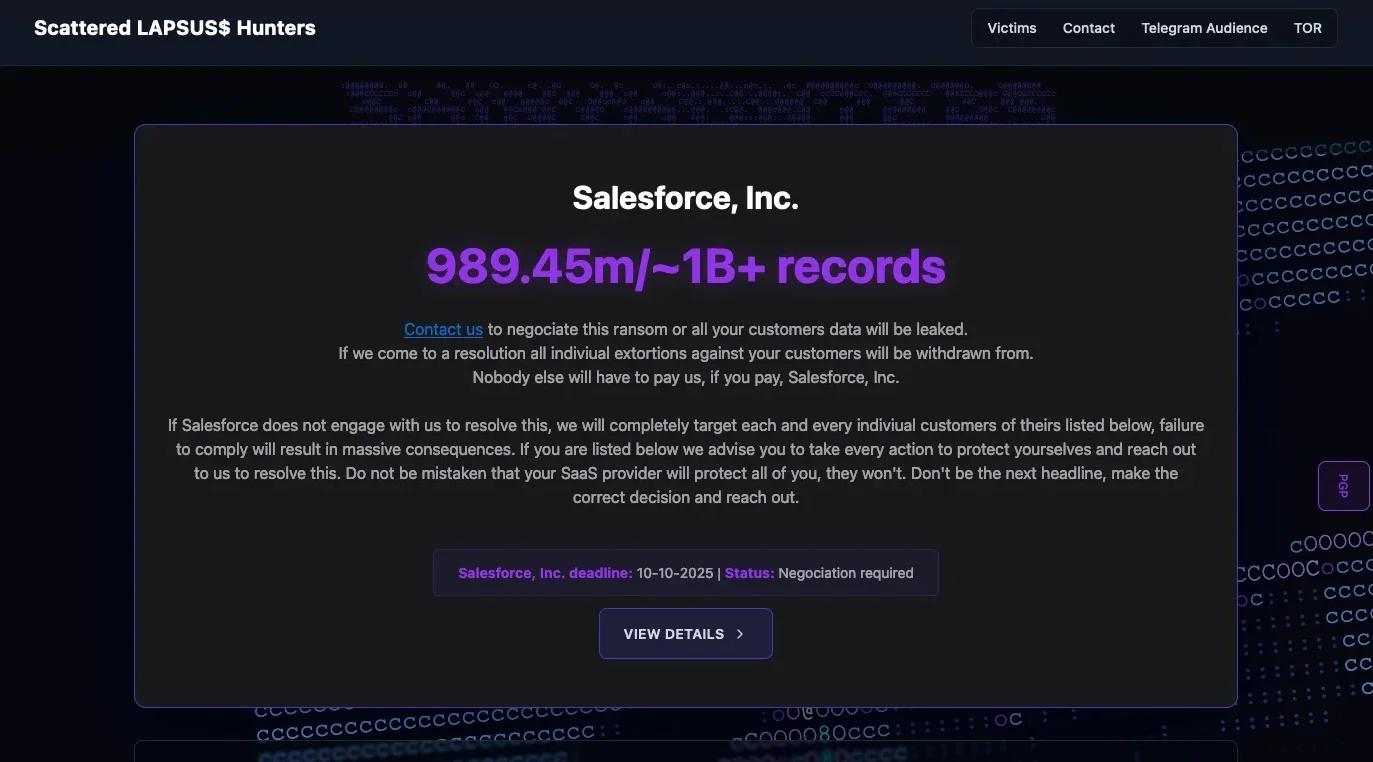
Scattered Lapsus$ Hunters launched a data leak site over the weekend, aiming to pressure organizations whose Salesforce databases they have…
Credential-based attacks happen in seconds. Learn how to block weak or stolen passwords instantly, safeguard accounts in real time, and…
The Cl0p extortion gang exploited multiple Oracle E-Business Suite (EBS) vulnerabilities, including one zero-day flaw (CVE-2025-61882), “to steal large amounts…
Many organizations still rely on weak authentication methods while workers’ personal habits create additional risks, according to Yubico. Training and…