Category: HelpnetSecurity
Imagine this: you’ve made it through the résumé screen, your skills look solid on paper, and now it’s interview day….
Hospitals, airports, and campuses are no longer dealing with separate security problems. Someone can slip past a checkpoint while another…
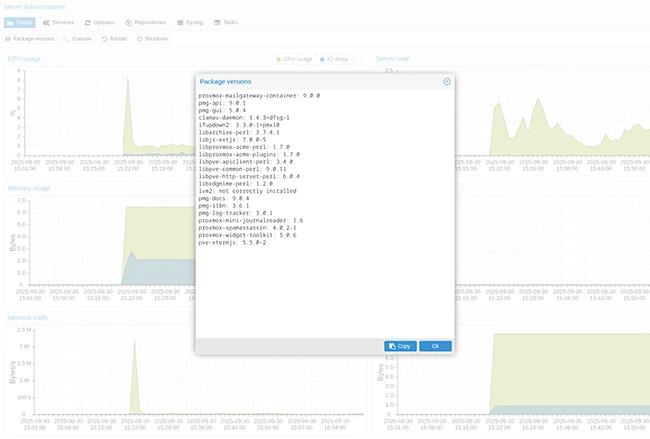
First released in 2005, the open-source Proxmox Mail Gateway has become a widely adopted mail proxy, positioned between the firewall…
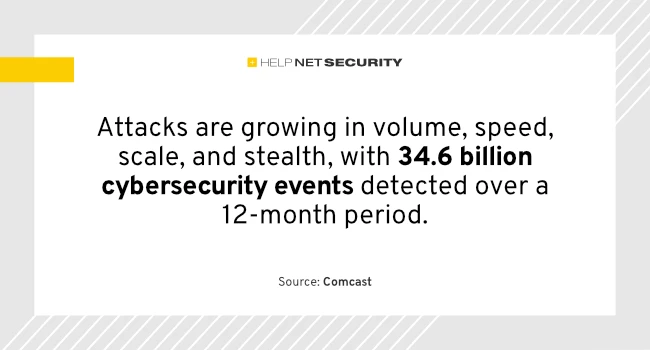
The volume of cyberattacks has reached staggering levels, with new tactics that blur the line between legitimate and malicious activity….
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Keeping the internet afloat: How…
Protegrity Developer Edition enables developers, data scientists, ML engineers, and security teams an easy way to add data protection into…
You probably think twice before downloading a random app or opening an unfamiliar email attachment. But how often do you…
Apple’s release of macOS 26 Tahoe introduced a new disk image format and updated an older one, both of which…
Americans are dealing with a growing wave of digital scams, and many are losing money in the process. According to…
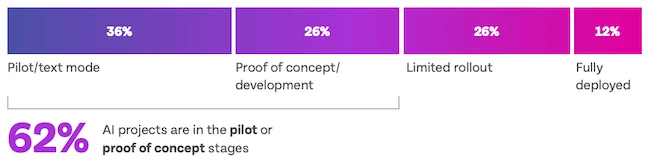
Companies are pouring money into AI for IT operations, but most projects are still far from maturity. A global survey…
Here’s a look at the most interesting products from the past week, featuring releases from Acronis, Legit Security, NowSecure, Siemens,…
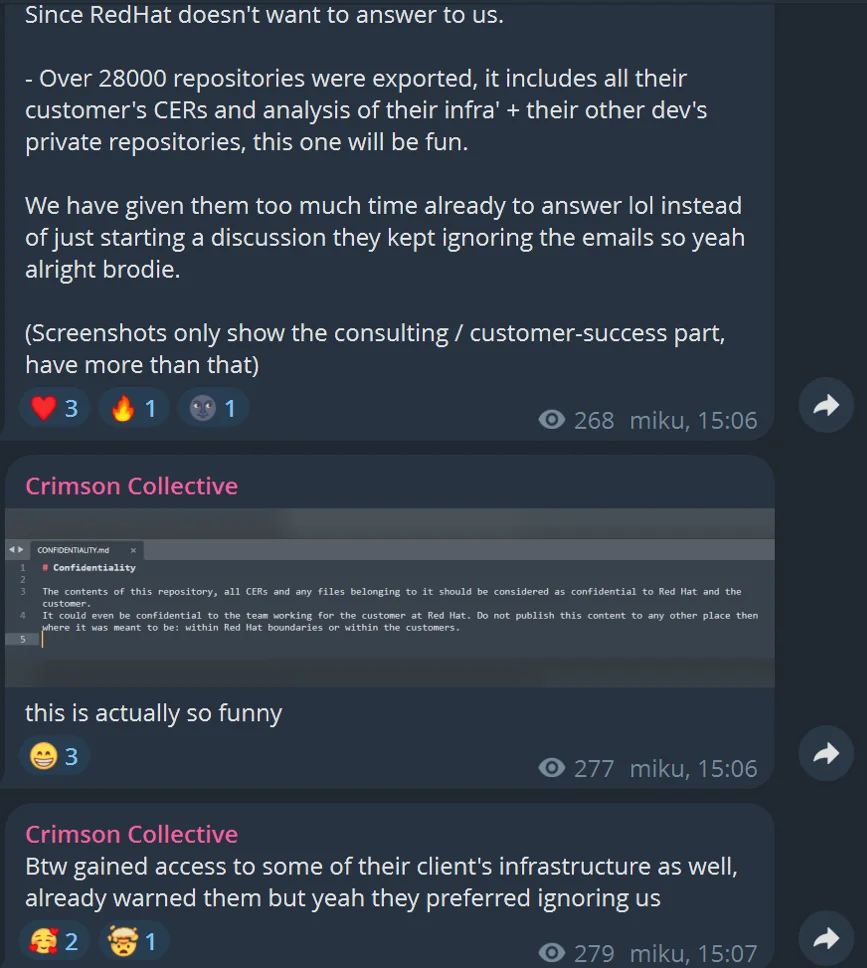
The Crimson Collective, an emerging extortion / hacker group, has made a bombshell claim on their Telegram channel: they have…