Category: HelpnetSecurity
The OpenSSL Project has announced the release of OpenSSL 3.6.0, a feature update that brings significant functionality improvements, standards compliance,…
Unknown attackers claiming affiliation with the Cl0p extortion gang are hitting business and IT executives at various companies with emails…
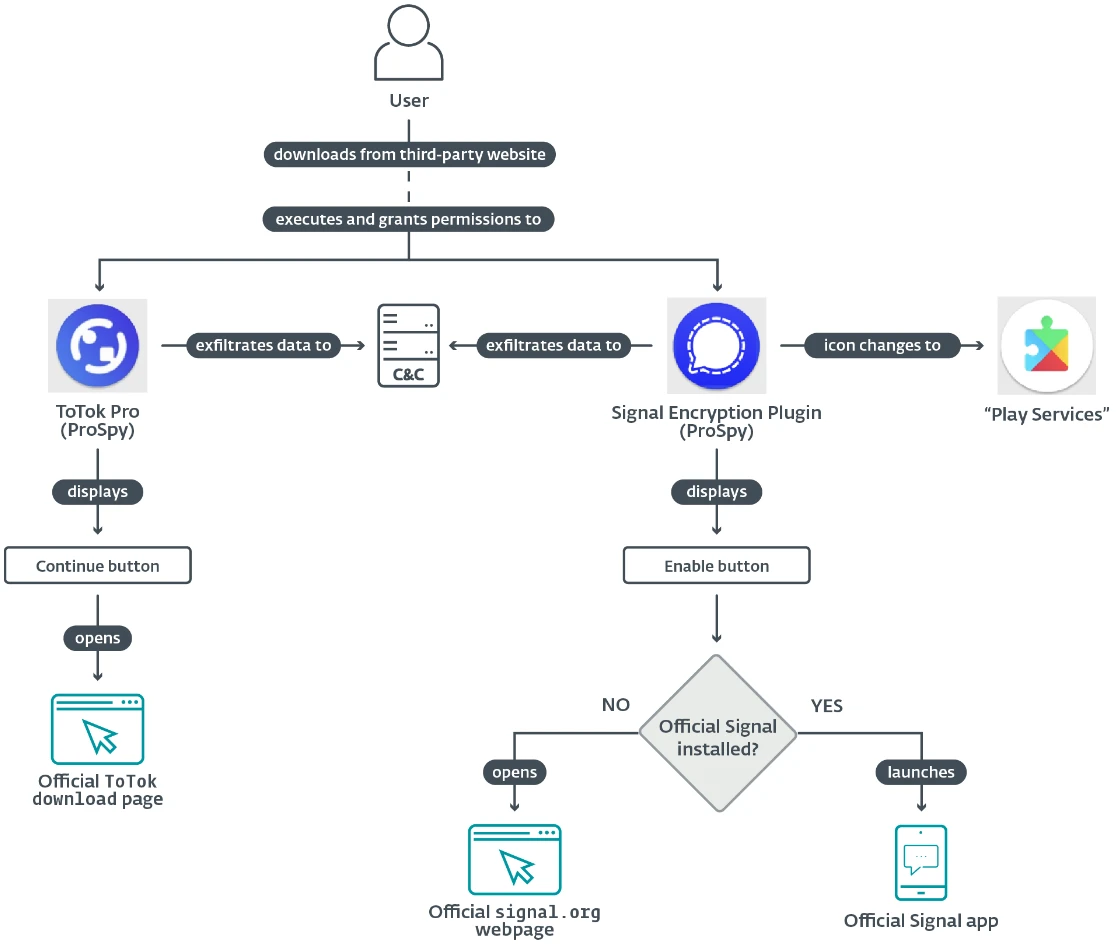
ESET researchers have found two Android spyware campaigns aimed at people looking for secure messaging apps such as Signal and…
Underwriting is undergoing a major transformation as financial institutions push for faster decisions, better fraud detection, and greater personalization, according…
Checkov is an open-source tool designed to help teams secure their cloud infrastructure and code. At its core, it’s a…
In this Help Net Security interview, Robert Sullivan, CIO & CISO at Agero, shares his perspective on automotive cybersecurity. He…
LLMs and agentic systems already shine at everyday productivity, including transcribing and summarizing meetings, extracting action items, prioritizing critical emails,…
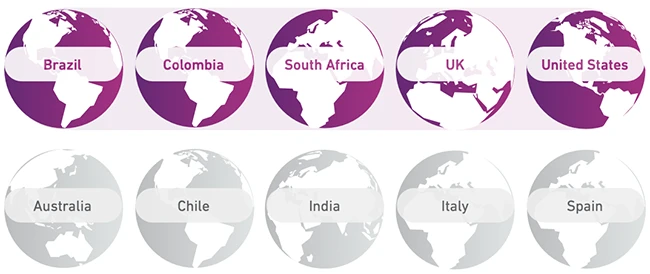
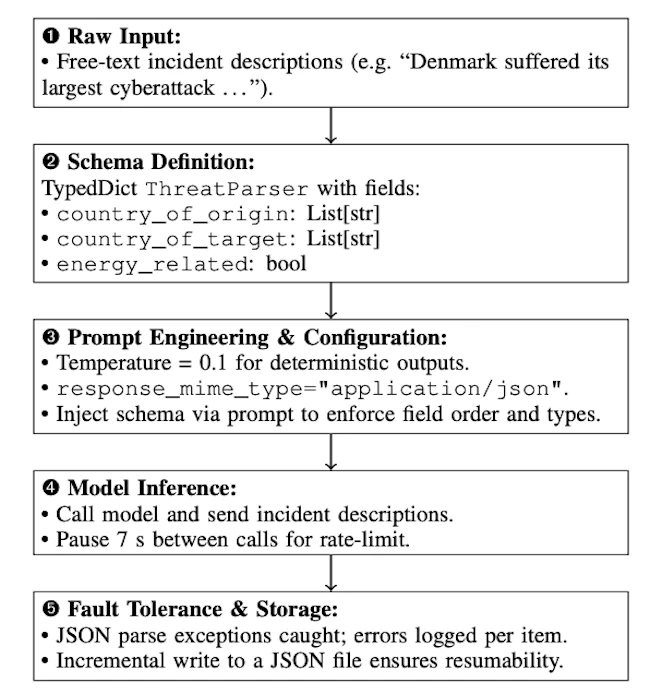
A new study from the Karlsruhe Institute of Technology shows how geopolitical tensions shape cyberattacks on power grids, fuel systems,…
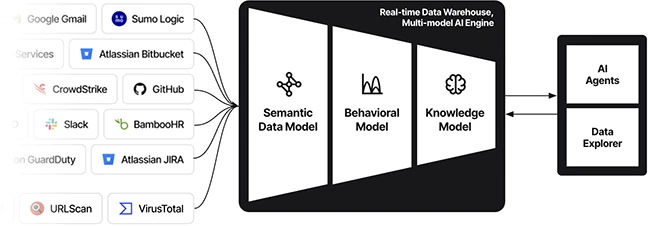
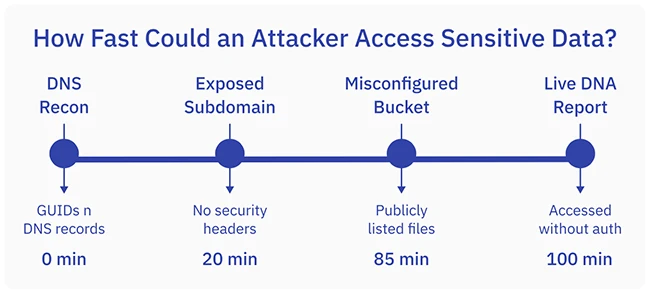
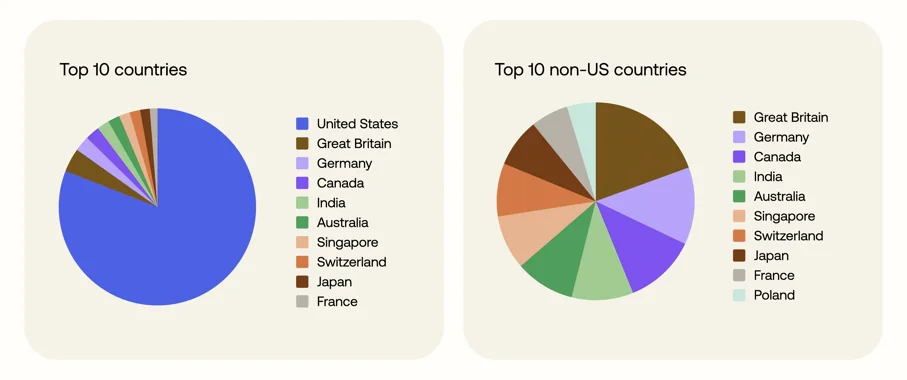
A new security posture report on the biotech sector shows how quickly attackers could reach sensitive health data with only…
North Korea’s clandestine IT Worker (ITW) program, which is long known for targeting U.S. technology firms and crypto firms, has…
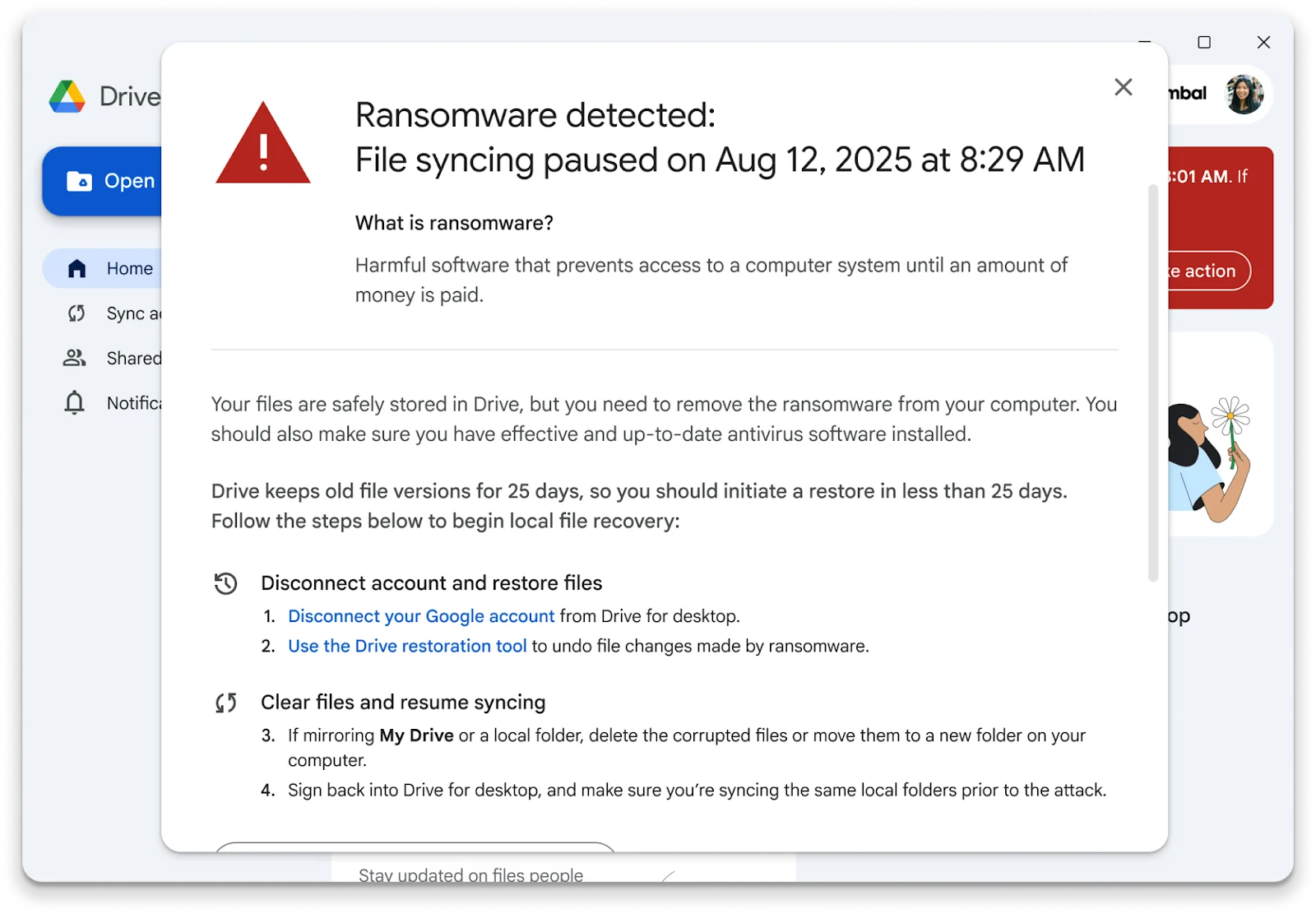
Google has rolled out AI-powered ransomware detection and file restoration features in Drive for desktop, Google’s official file syncing and…
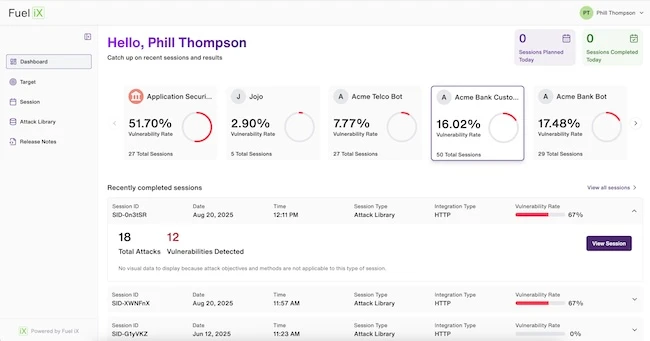
TELUS Digital has released its continuous automated red-teaming application, Fuel iX Fortify. The solution helps enterprises test GenAI systems at…