Category: HelpnetSecurity
Despite Cisco and various cybersecurity agencies warning about attackers actively exploting zero-day vulnerabilities (CVE-2025-20333 and CVE-2025-20362) in Cisco Adaptive Security…
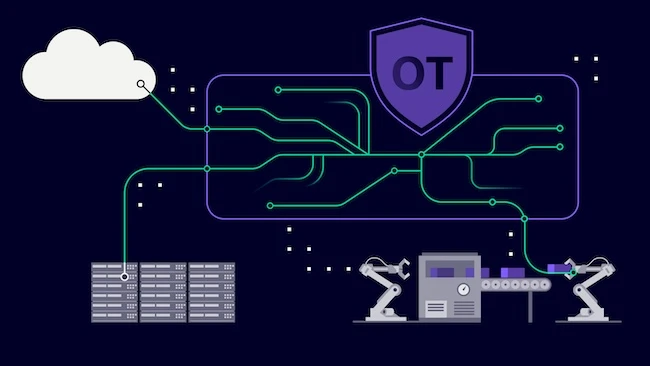
Siemens launched SINEC Secure Connect, the zero trust security platform designed for operational technology (OT) networks. The software solution virtualizes…
Biometric technologies were originally designed to improve security and streamline authentication, but they’re often misused in ways most people don’t…
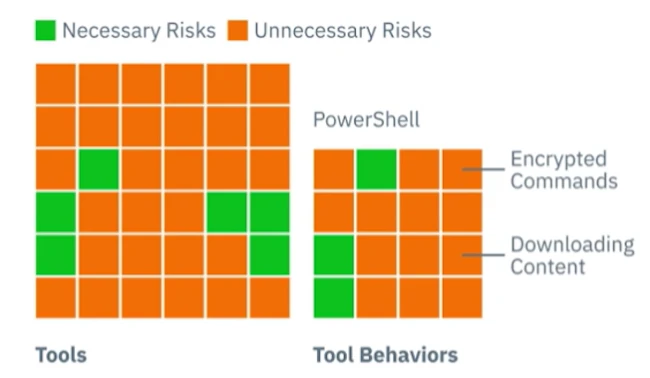
Every time cyber defenders and companies discover new ways to block intrusions, attackers change their tactics and find a way…
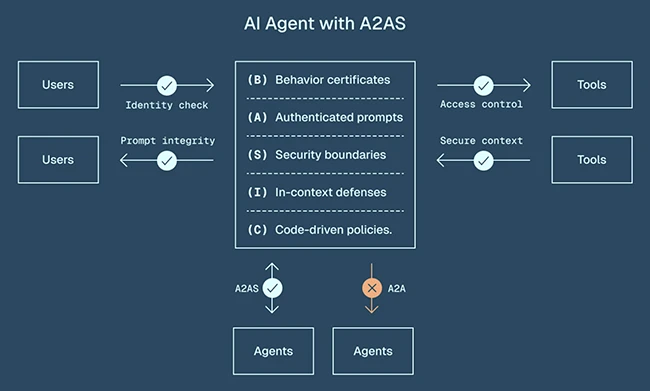
AI systems are now deeply embedded in business operations, and this introduces new security risks that traditional controls are not…
Cyber threats are shifting in 2025, and while large companies are still targets, attackers are turning their attention to smaller…
The cooperative agreement between the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the not-for-profit Center for Internet Security is…
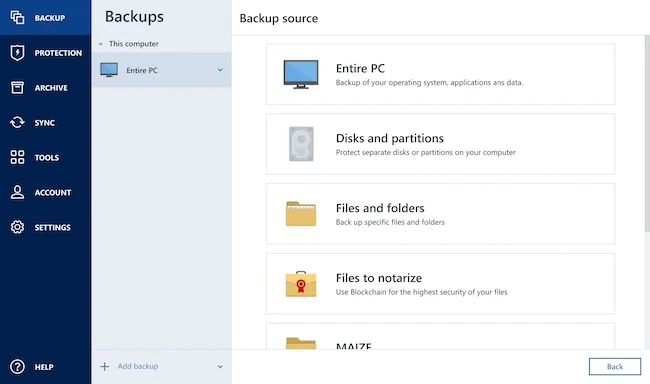
Acronis announced the general availability of Acronis True Image 2026, the new release of its natively integrated backup and security…
Join Picus Security, SANS, Hacker Valley, and leading CISOs at The BAS Summit 2025 to learn how AI is redefining…
Western Digital has fixed a critical remote code execution vulnerability (CVE-2025-30247) in the firmware powering its My Cloud network-attached storage…
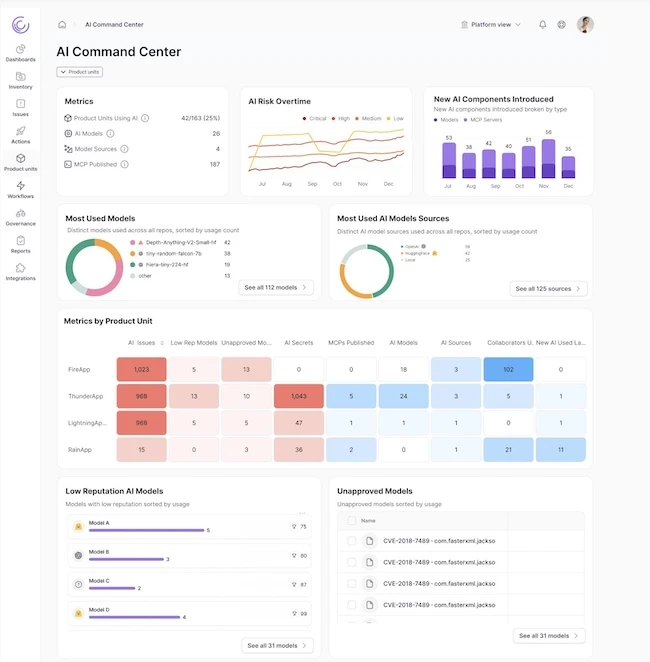
Legit Security has updated its AI Security Command Center. As vibe coding and AI-first development reshape how software is built,…
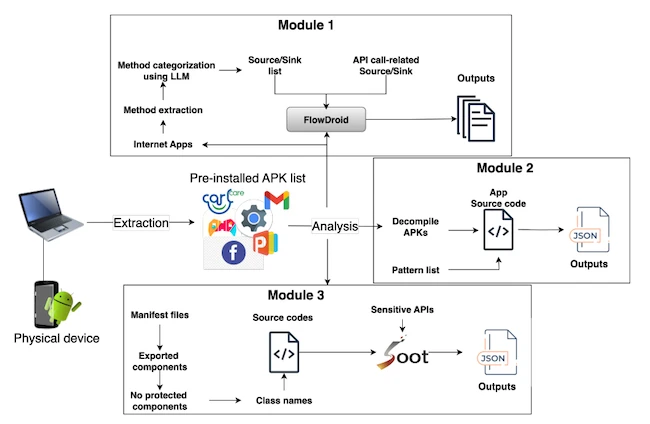
Researchers have found that many low-cost Android devices come with pre-installed apps that have high-level access to the system. Unlike…