Category: HelpnetSecurity
A widespread campaign aimed at breaching organizations via zero-day vulnerabilities in Cisco Adaptive Security Appliances (ASA) has been revealed by…
Here’s a look at the most interesting products from the past month, featuring releases from: Absolute Security, Blackdot Solutions, Catchpoint,…
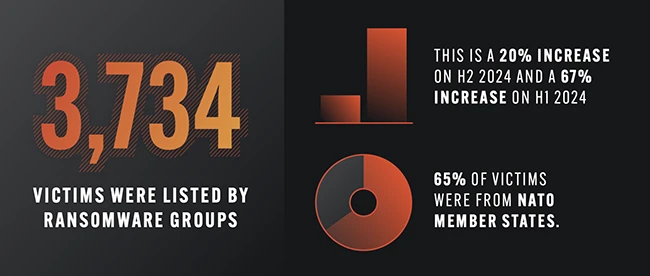
Ransomware activity is climbing again, with a steep increase in the number of victims and the number of groups launching…
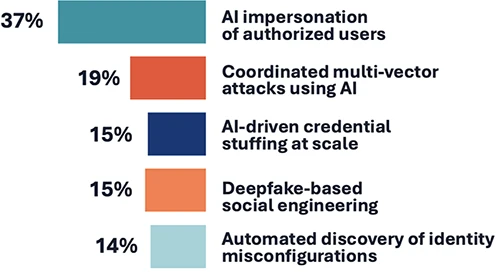
Instead of going after software flaws or network weaknesses, attackers are targeting something much easier to steal: identity credentials. A…
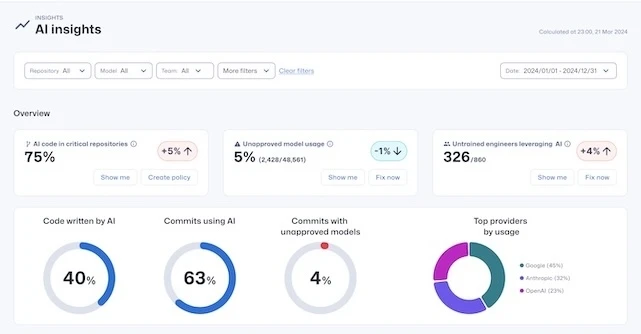
AI agents are becoming more common in the workplace, but giving them access to sensitive systems can be risky. Credentials…
In this Help Net Security video, David Norlin, CTO of Lumifi, explores the role of agentic AI in the security…
Windows 10 users in the European Economic Area (EEA) will be able to receive extended security updates until October 14,…
Cybercriminals are increasingly using AI-powered tools and (malicious) large language models to create convincing, error-free emails, deepfakes, online personas, lookalike/fake…
ESET Research has published new findings on DeceptiveDevelopment, also called Contagious Interview. This North Korea-aligned group has become more active…
Sensitive data is everywhere and growing fast. A new report from Concentric AI highlights how unstructured data, duplicate files, and…
Secure Code Warrior has launched a beta program to expand the AI capabilities of its Trust Agent product. The new…
Drones have already shown their impact in military operations, and their influence is spreading across the agricultural and industrial sectors….