Category: HelpnetSecurity
Distributed denial-of-service (DDoS) attacks remain one of the most common and disruptive forms of cybercrime. Defenders have traditionally focused on…
Authorities around the world have recovered $439 million from criminals following a months-long operation led by INTERPOL. The effort, called…
Managing security across dozens or even hundreds of SaaS apps has become a major headache. Each tool has its own…
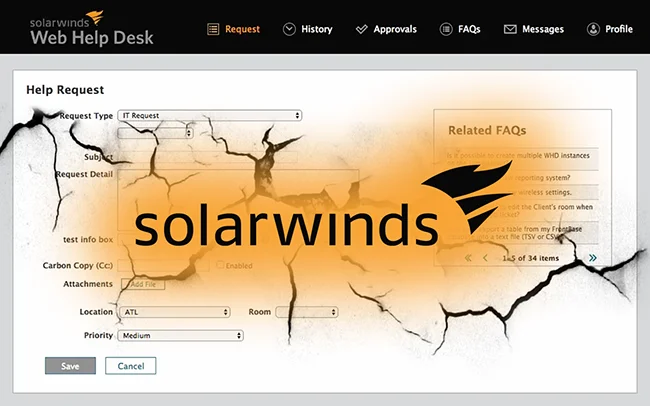
SolarWinds has fixed yet another unauthenticated remote code execution vulnerability (CVE-2025-26399) in Web Help Desk (WHD), its popular web-based IT…
Suspected state-sponsored attackers have exploited a zero-day vulnerability (CVE-2025-59689) in the Libraesva Email Security Gateway (ESG), the Italian email security…
Teleport released AI Session Summaries, a new capability in Teleport Identity Security that enables customers to summarize insights from thousands…
A cross-border cryptocurrency scam has left investors across Europe with losses of more than €100 million. Authorities in several countries…
OffSec has released Kali Linux 2025.3, the most up-to-date version of its popular penetration testing and digital forensics platform. What’s…
Attackers have a new favorite playground, and it’s not where many security teams are looking. According to fresh data from…
In this Help Net Security interview, Tim Bramble, Director of Threat Detection and Response at OpenText, discusses how SOC teams…
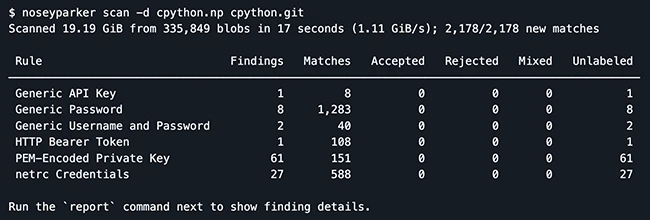
Nosey Parker is an open-source command-line tool that helps find secrets and sensitive information hidden in text files. It works…
In this Help Net Security video, David Hardoon, Global Head of AI Enablement at Standard Chartered, discusses the role of…