Category: HelpnetSecurity
CVE-2025-11371, a unauthenticated Local File Inclusion vulnerability in Gladinet CentreStack and Triofox file-sharing and remote access platforms, is being exploited…
A lot of classic software is reaching end-of-life (EOL) this month. Windows 10, Office 2016 and Exchange Server 2016 have…
SMBs may not have big budgets, but they are on the receiving end of many cyberattacks. A new study from…
Nagios is an open-source monitoring solution, now included as part of the robust Nagios Core Services Platform (CSP). It delivers…
Here’s a look at the most interesting products from the past week, featuring releases from Object First, OPSWAT, Radiflow, and…
Threat actors are using an increasing variety of commercial and open-source products to carry out their attacks: according to researchers,…
The attackers who brute-forced their way into SonicWall’s firewall cloud backup service accessed configuration backup files of all customers who…
Semperis released Ready1 for Identity Crisis Management, which combines its Active Directory Forest Recovery (ADFR), Disaster Recovery for Entra Tenant…
Object First unveiled Ootbi Mini, a new compact immutable storage appliance designed for remote and branch offices, edge environments, and…
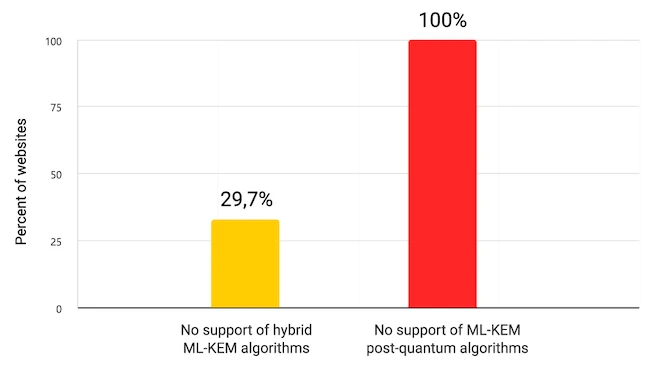
The cryptocurrency sector faces an existential threat on two fronts: none of the 2,138 web applications and 146 mobile apps…
Scam websites tied to online shopping, pet sales, and other e-commerce schemes continue to cause millions in losses each year….
In this Help Net Security interview, Jess Vachon, CISO at PRA Group, discusses the company’s multi-layered defense against fraud and…