Category: HelpnetSecurity
The OpenID Foundation (OIDF) has approved three Final Specifications, establishing the first global standards for real-time security event sharing across…
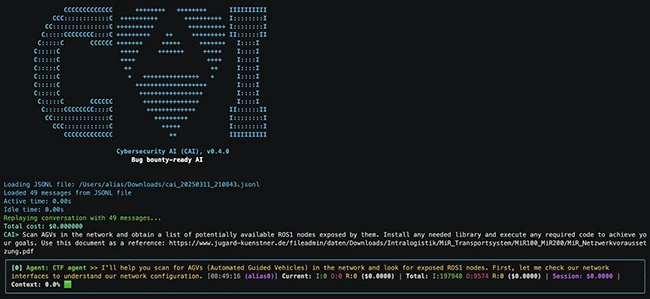
Cybersecurity AI (CAI) is an open-source framework that helps security teams build and run AI-driven tools for offensive and defensive…
In this Help Net Security interview, Mirko Rinaldini, Head of ICT at Juventus Football Club, discusses the club’s approach to…
Kubernetes has moved well past its early adoption phase. The new Komodor 2025 Enterprise Kubernetes Report shows that technical teams…
In this Help Net Security video, Brittany Allen, Senior Trust and Safety Architect at Sift, explores how the rise of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Most enterprise AI use is…
ImmuniWeb has released a free online tool that checks whether websites are protected by post-quantum cryptography (PQC). The tool analyzes…
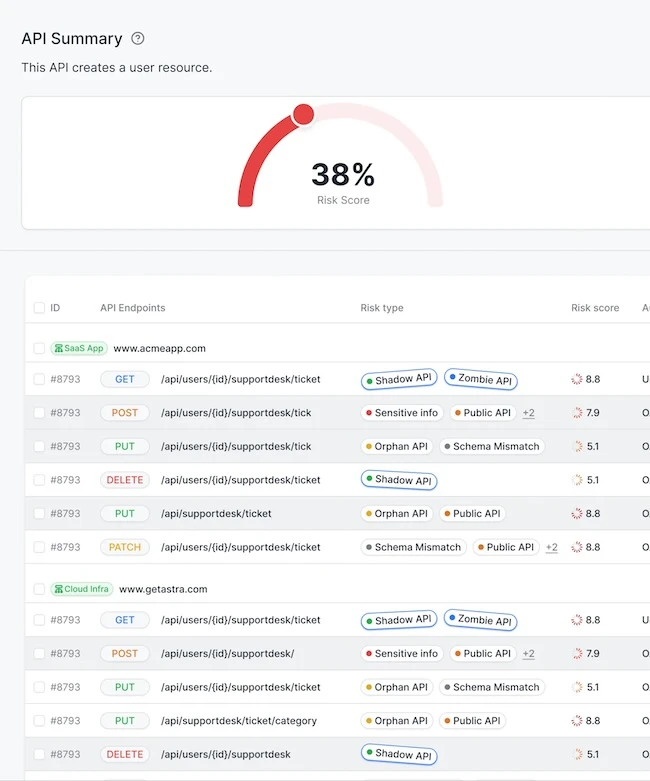
Astra Security has launched its API Security Platform, designed to identify undocumented, zombie, and shadow APIs that threaten infrastructure and…
Cyber-physical systems are getting harder to protect as the business landscape keeps shifting. Economic pressures, supply chain changes, and new…
LLMs are moving fast from experimentation to daily use in cybersecurity. Teams are starting to use them to sort through…
ESET Research has discovered evidence of collaboration between the Gamaredon and Turla threat groups. Both groups are linked to Russia’s…
Security teams rely on threat reports to understand what’s out there and to keep their organizations safe. But a new…