Category: HelpnetSecurity
Here’s a look at the most interesting products from the past week, featuring releases from Absolute Security, Catchpoint, Nagomi Security,…
Between attackers exploiting 0-day and n-day vulnerabilities in the company’s firewalls and Secure Mobile Access appliances, SonicWall and its customers…
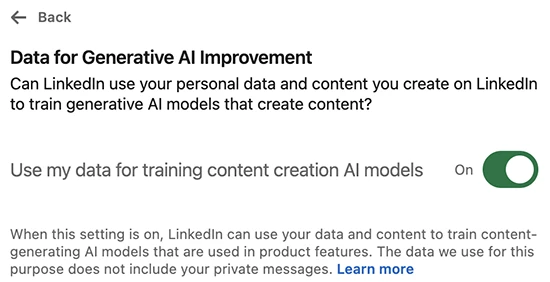
LinkedIn is making major changes to its User Agreement and Privacy Policy, effective November 3, 2025. Among the most notable…
Google has released a security update for the Chrome stable channel to fix a zero‑day vulnerability (CVE-2025-10585) reported by its…
The first half of 2025 saw one of the worst waves of crypto hacks to date, with more than $3.01…
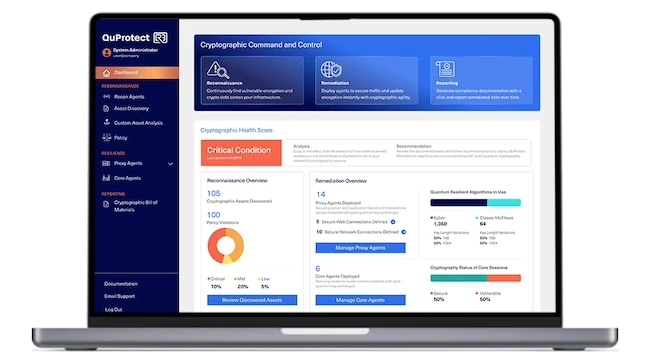
QuSecure launched QuProtect R3, an integrated, production-ready PQC platform designed to simplify encryption modernization for everyone. With the platform’s Reconnaissance…
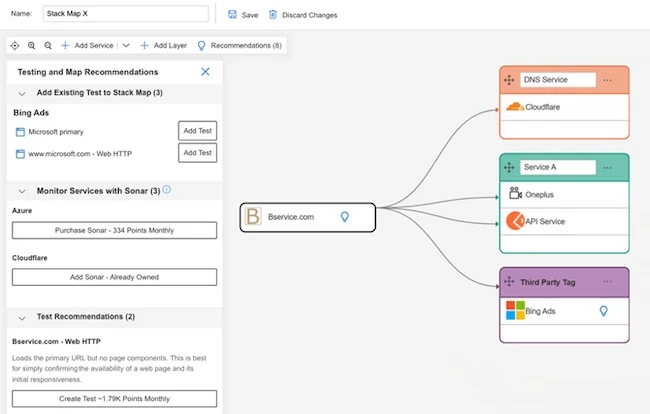
Catchpoint released two AI-powered capabilities designed to simplify digital resilience for critical applications: Catchpoint Root Cause Analysis (RCA) and Catchpoint…
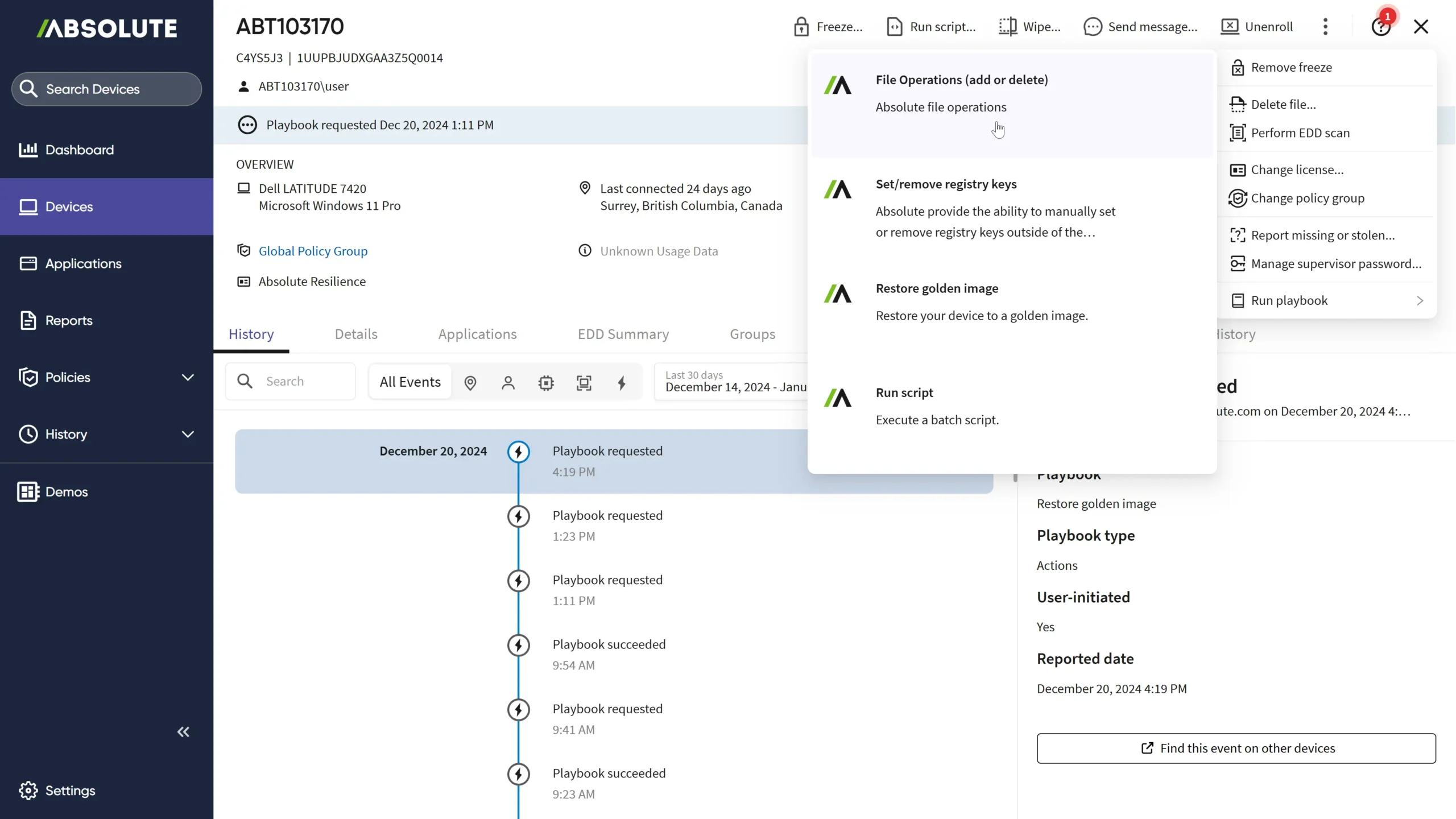
Absolute Security released Rehydrate, empowering enterprises to recover from IT or cyber incidents remotely and at scale to minimize operational…
In this Help Net Security interview, Daniel Stenberg, lead developer od cURL, discusses how the widely used tool remains secure…
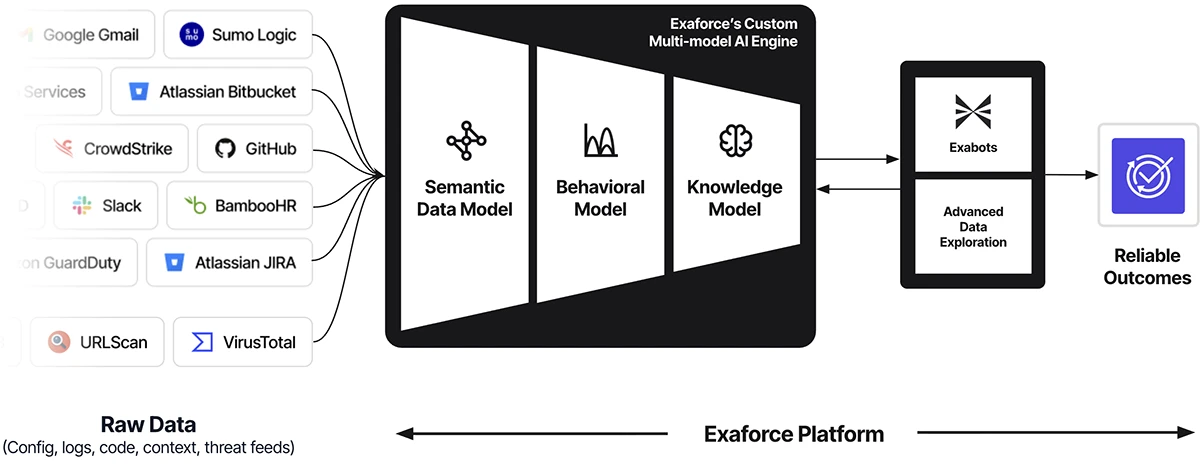
Today’s SOCs face an impossible equation: too much noise, too many gaps, and too few hands. Detection coverage gaps leave…
Cybersecurity leaders know the attack surface has been growing for years, but the latest State of Information Security Report 2025…
Hiring new employees has always carried some risk, but that risk is growing in new ways, and identity fraud is…