Category: HelpnetSecurity
Despite having been discovered and reported in 2014, the vulnerability that allows pixie dust attacks still impacts consumer and SOHO…
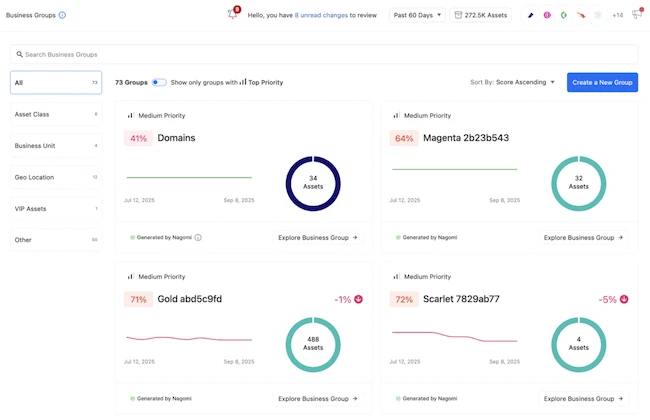
Nagomi Security announced the next step in its platform evolution with Nagomi Control, a new release that enhances Continuous Threat…
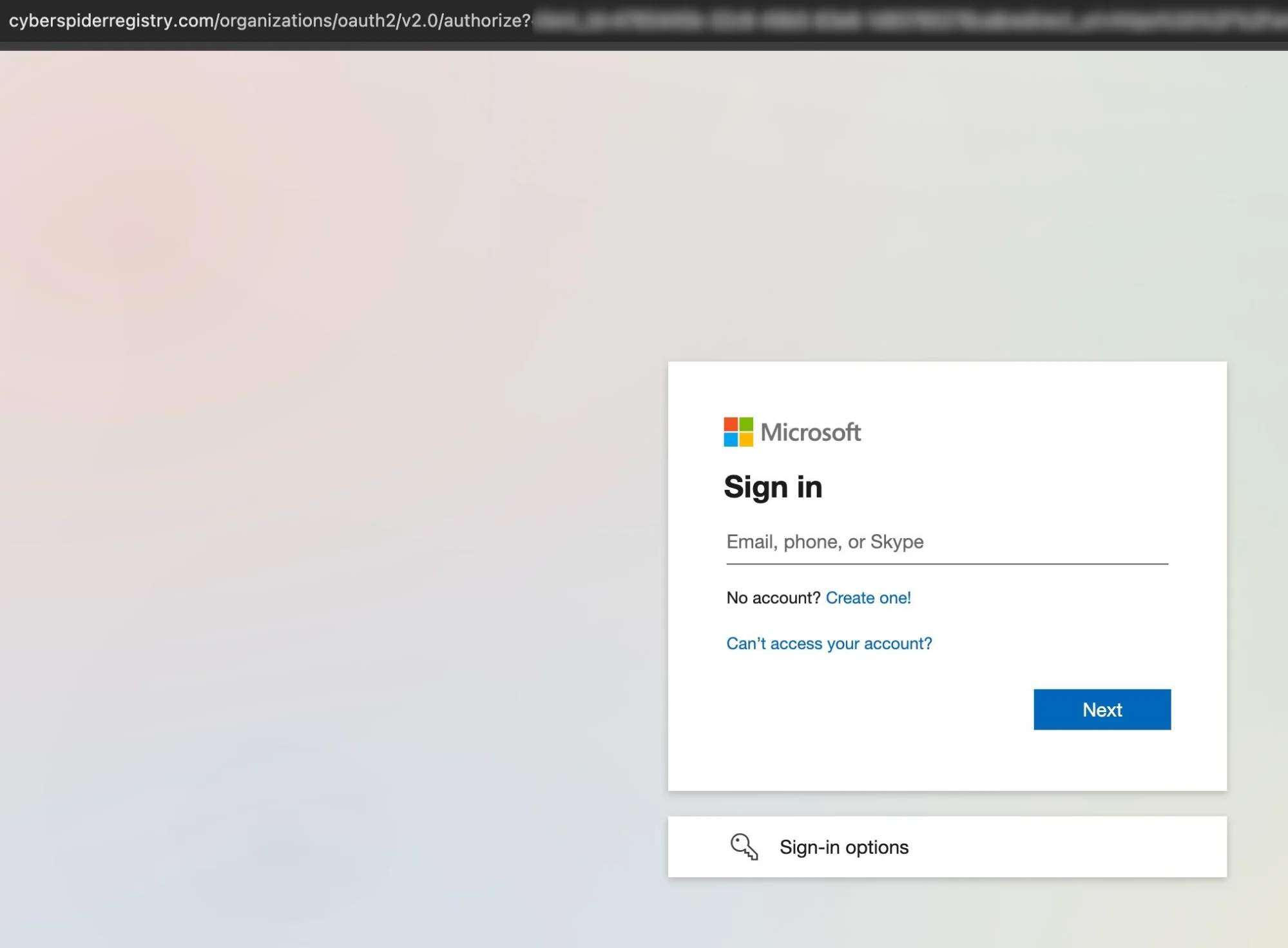
Microsoft and Cloudflare have disrupted a Phishing-as-a-Service operation selling the RaccoonO365 kit for stealing Microsoft 365 account credentials. “Using a…
Siren announced the launch of K9, an AI companion designed to transform the way investigators uncover threats and connections. K9…
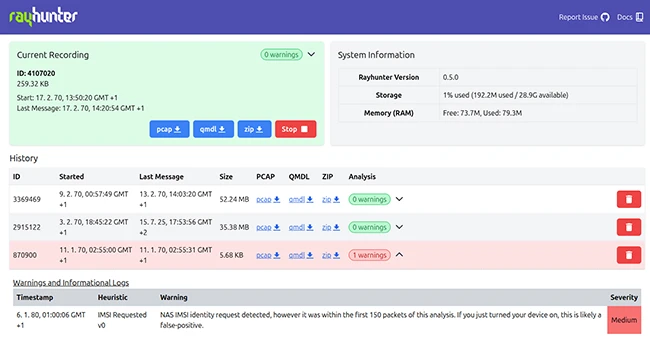
The Electronic Frontier Foundation (EFF) has released Rayhunter, a new open-source tool designed to detect cell site simulators (CSS). These…
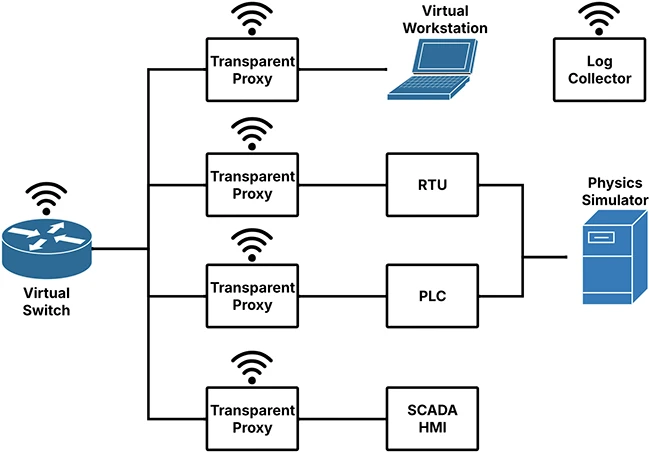
Researchers have introduced a new way to study and defend against ICS threats. Their project, called ICSLure, is a honeynet…
In this Help Net Security interview, Marco Goldberg, Managing Director at EQS Group, discusses how compliance and regulation are evolving…
In this Help Net Security video, Jérôme Segura, VP of Threat Research at Datadome, explains why intent, not just identifying…
Attackers are finding new ways to blend in with everyday business tools, hiding their activity inside formats and processes that…
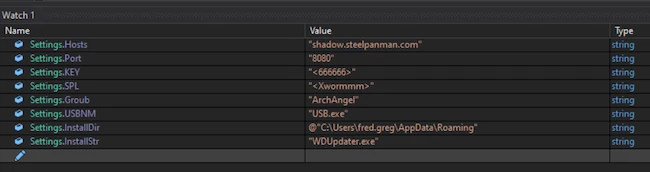
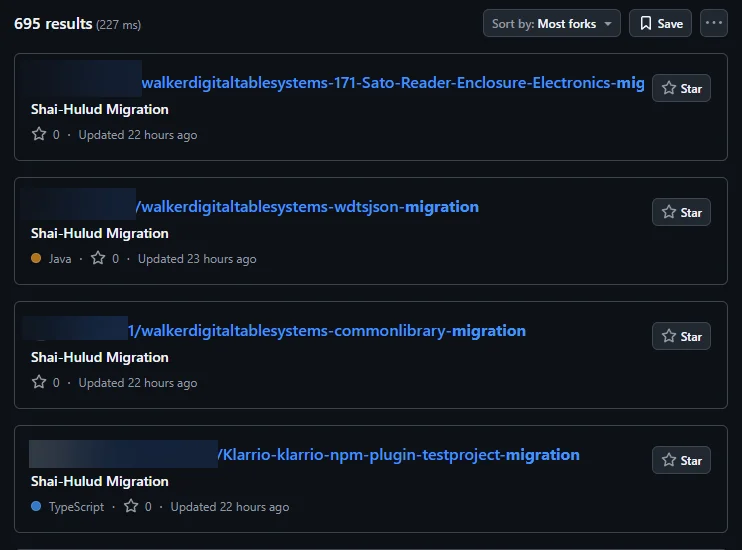
A potentially monumental supply chain attack is underway, thanks to a self-replicating worm-like payload that has been compromising packages published…
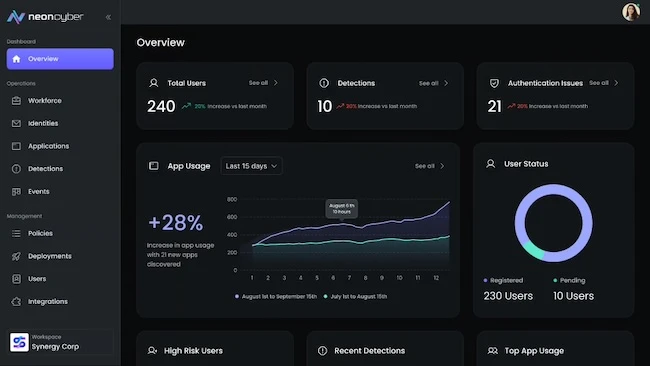
Neon Cyber announced its emergence from stealth and unveiled the first Workforce Cybersecurity Platform (WCP), delivering protection across browsers, SaaS…
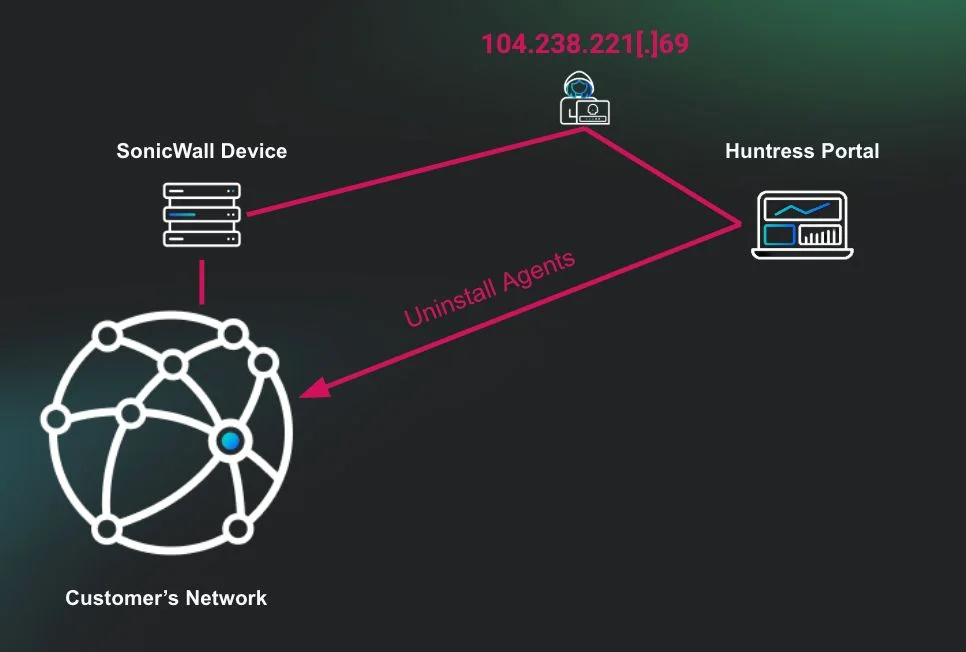
All target organizations are different, but ransomware attackers are highly adaptive and appreciate – and will exploit – any mistake…