Category: HelpnetSecurity
GitHub is adding post-quantum cryptography to secure SSH connections, a move that signals the company’s preparation for a time when…
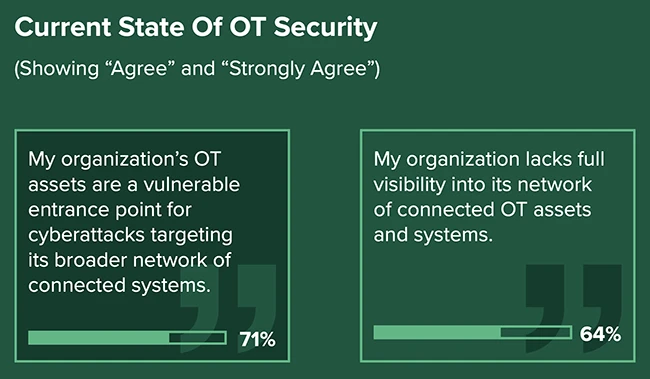
Cyberattacks keep hitting the OT systems that critical infrastructure operators run, according to new research from Forrester. In a survey…
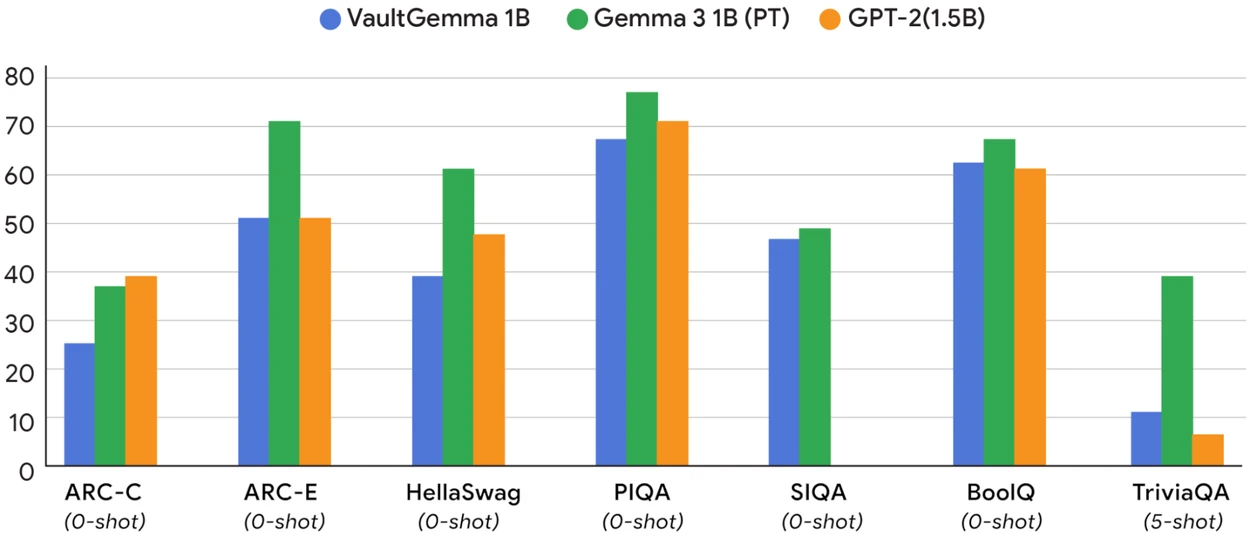
Google has released VaultGemma, a large language model designed to keep sensitive data private during training. The model uses differential…
In this Help Net Security interview, Nir Rothenberg, CISO at Rapyd, discusses global differences in payment security maturity and the…
AI-powered video surveillance brings up big questions about privacy. On one hand, it can make us feel safer, but on…
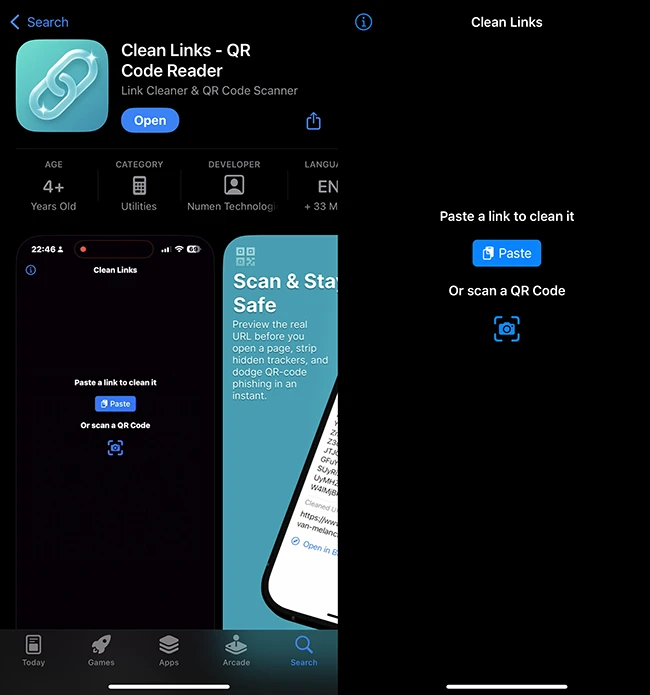
Clean Links is a handy app that shows you exactly where a link will take you before you click it….
CISO Haier Europe | Italy | On-site – View job details As a CISO, you will develop an information security…
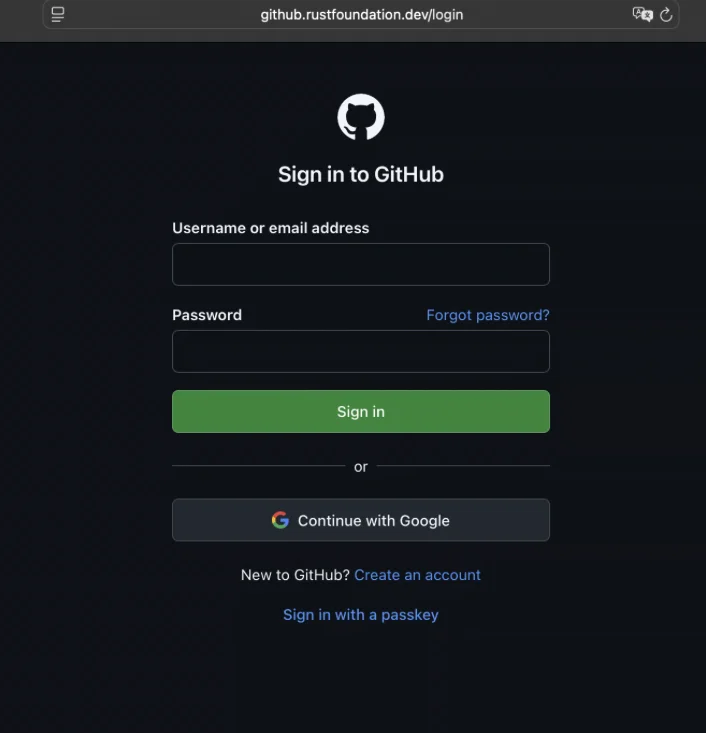
Developers publishing crates (binaries and libraries written in Rust) on crates.io, Rust’s main public package registry, have been targeted with…
Most enterprise AI activity is happening without the knowledge of IT and security teams. According to Lanai, 89% of AI…
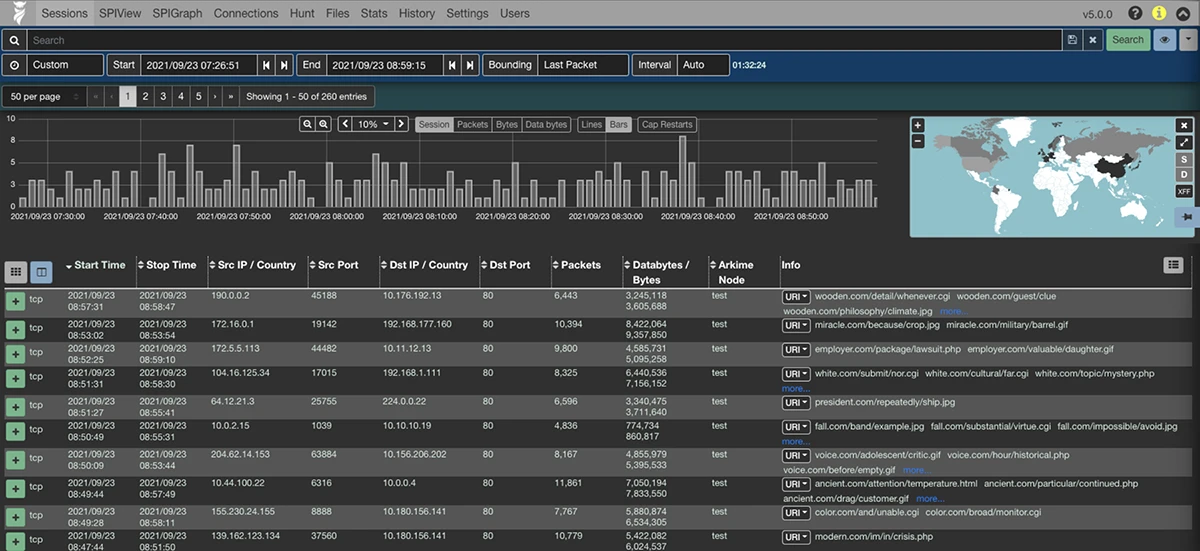
Arkime is an open-source system for large-scale network analysis and packet capture. It works with your existing security tools to…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Salesloft Drift data breach: Investigation…
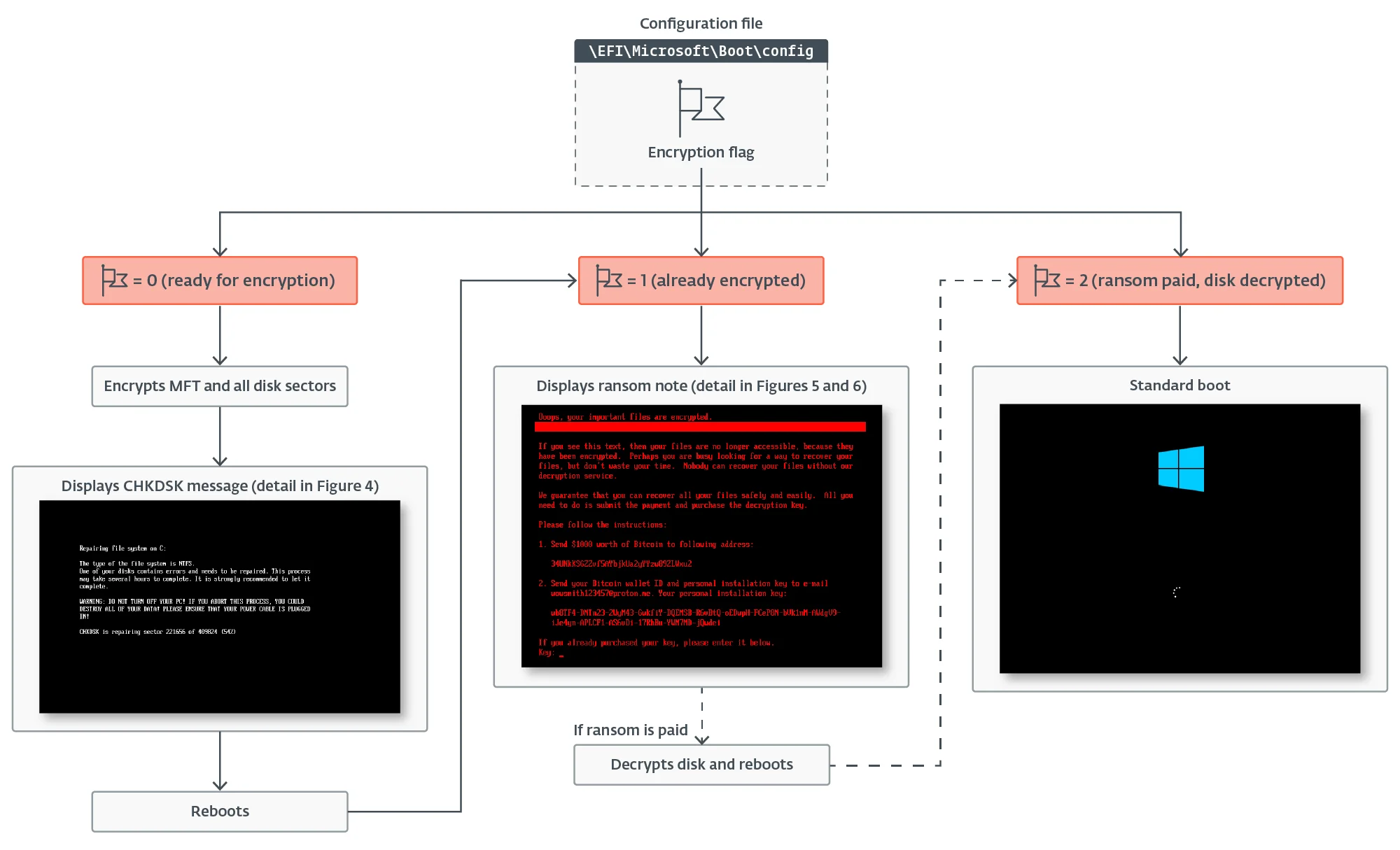
ESET researchers have discovered HybridPetya, a bootkit-and-ransomware combo that’s a copycat of the infamous Petya/NotPetya malware, augmented with the capability…