Category: HelpnetSecurity
The US Cybersecurity and Infrastructure Security Agency (CISA) has affirmed its continuing support for the Common Vulnerabilities and Exposures (CVE)…
In the pharmaceutical industry, clinical trial data, patient records, and proprietary drug formulas are prime targets for cybercriminals. These high-value…
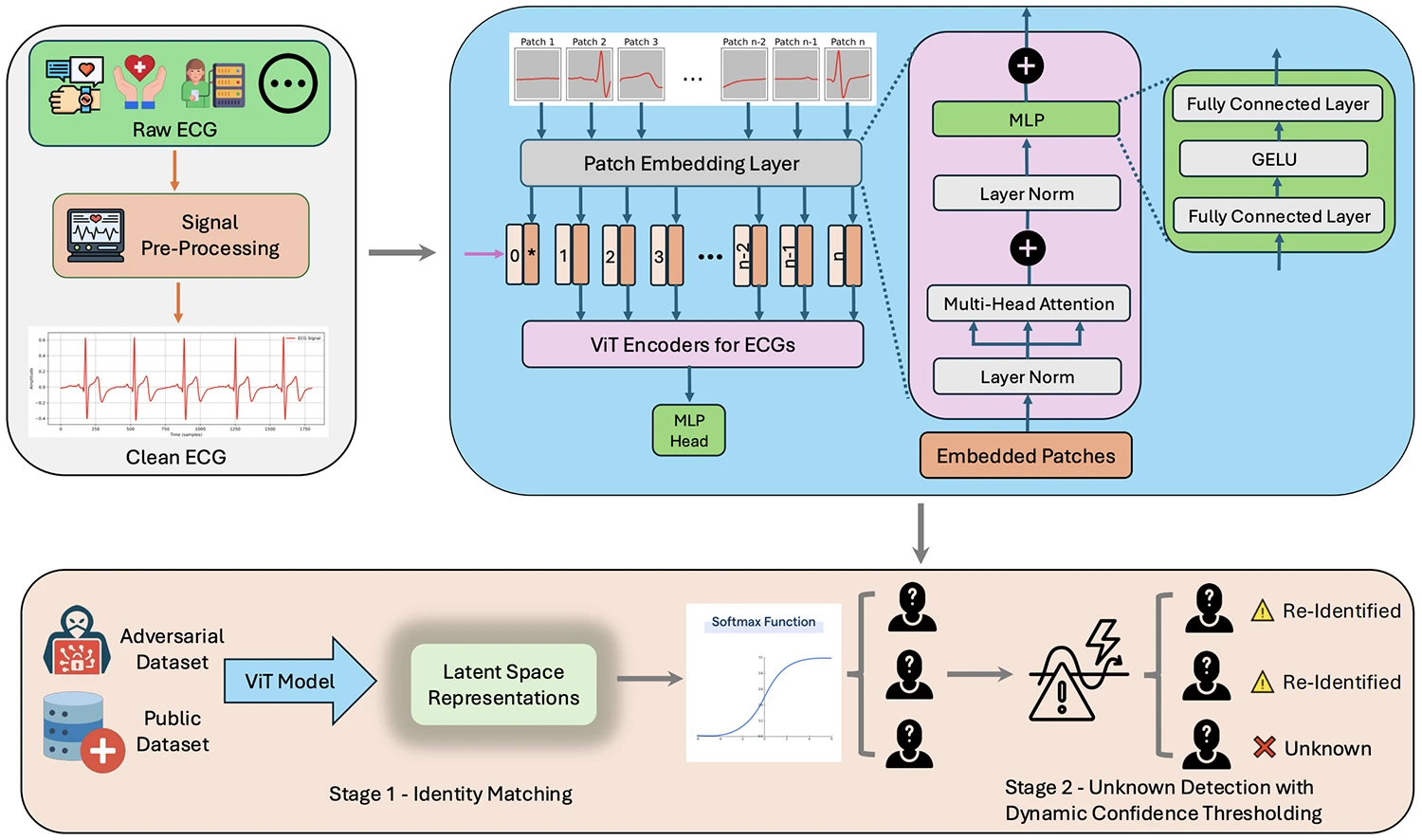
A new study has found that electrocardiogram (ECG) signals, often shared publicly for medical research, can be linked back to…
AI is being added to business processes faster than it is being secured, creating a wide gap that attackers are…
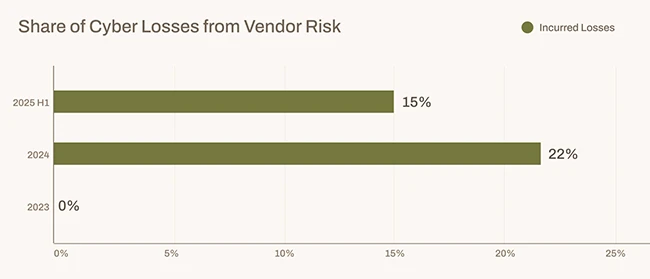
Ransomware, third-party disruptions, and the rise of AI-powered attacks are reshaping the cyber risk landscape in 2025. A new midyear…
Here’s a look at the most interesting products from the past week, featuring releases from Cynomi, DataLocker, Gigamon, Lookout, and…
Over a year after SonicWall patched CVE-2024-40766, a critical flaw in its next-gen firewalls, ransomware attackers are still gaining a…
An out-of-the-box setting in Cursor, a popular AI source-code editor, could be leveraged by attackers to covertly run malicious code…
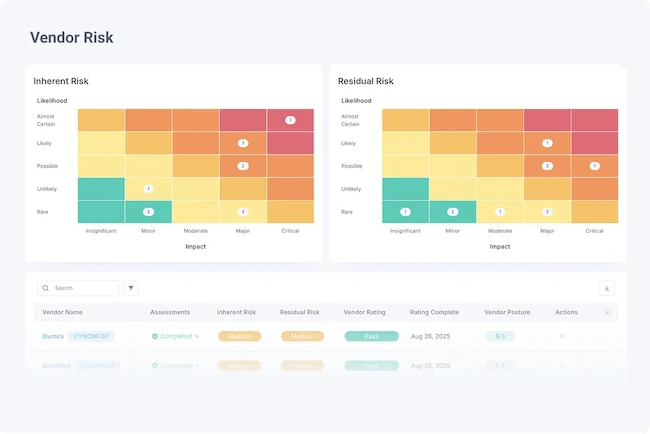
Cynomi has launched its Third-Party Risk Management (TPRM) module. Delivered as an add-on to the Cynomi vCISO Platform, the new…
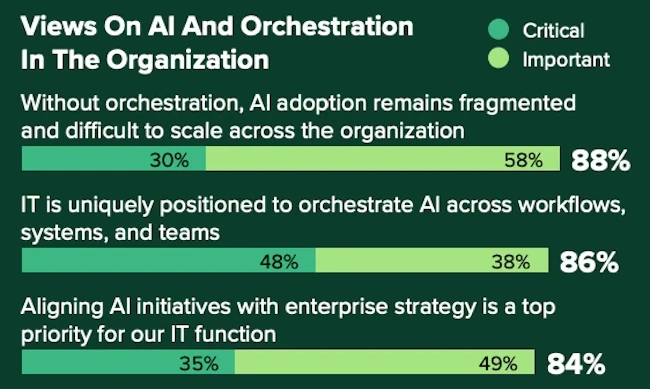
AI is being adopted across industries, but many organizations are hitting the same obstacles, according to Tines. IT leaders say…
You type your email address into a website form but never hit submit. Hours later, a marketing email shows up…
In this Help Net Security interview, Gregory Richardson, Vice President, Advisory CISO Worldwide, at BlackBerry, talks about the growing risks…