Category: HelpnetSecurity
In this Help Net Security video, John Wilson, Senior Fellow, Threat Research at Fortra, explores the state of DMARC adoption…
To succeed in the risk environment, risk, audit, and compliance leaders need to focus on what Gartner calls “reflexive risk…
Lookout introduces Smishing AI, an AI-powered solution designed to protect enterprises from the growing threat of SMS phishing (smishing) attacks….
On September 2025 Patch Tuesday, Microsoft has released patches for 80+ vulnerabilities in its various software products, but the good…
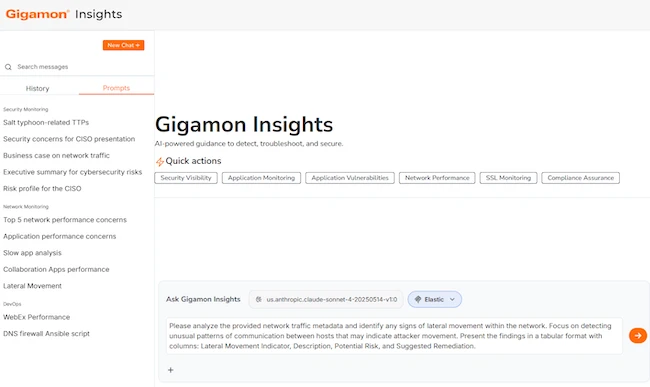
Gigamon has released Gigamon Insights, an agentic AI application purpose-built for network-derived telemetry that will deliver instant guidance for security…
AI agents are being deployed inside enterprises today to handle tasks across security operations. This shift creates new opportunities for…
Deception and media manipulation have always been part of warfare, but AI has taken them to a new level. Entrust…
LLMs can make mistakes, leak data, or be tricked into doing things they were not meant to do. Garak is…
Organizations often operate as if their security controls are fully effective simply because they’re deployed, configured, and monitored. Firewalls are…
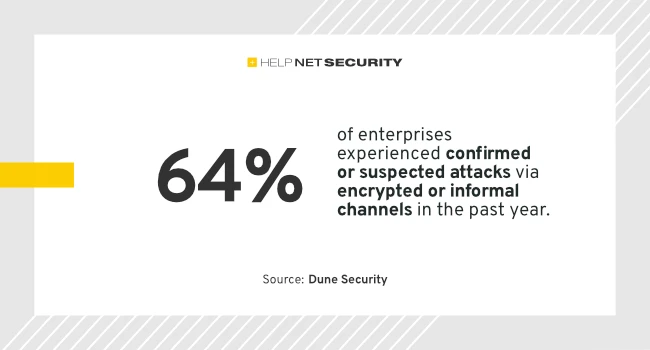
Breaches continue to grow in scale and speed, yet the weakest point remains unchanged: people. According to Dune Security’s 2025…
Media streaming company Plex has suffered a data breach and is urging users to reset their account password and enable…
Malicious versions of at least 18 widely used npm packages were uploaded to the npm Registry on Monday, following the…