Category: HelpnetSecurity
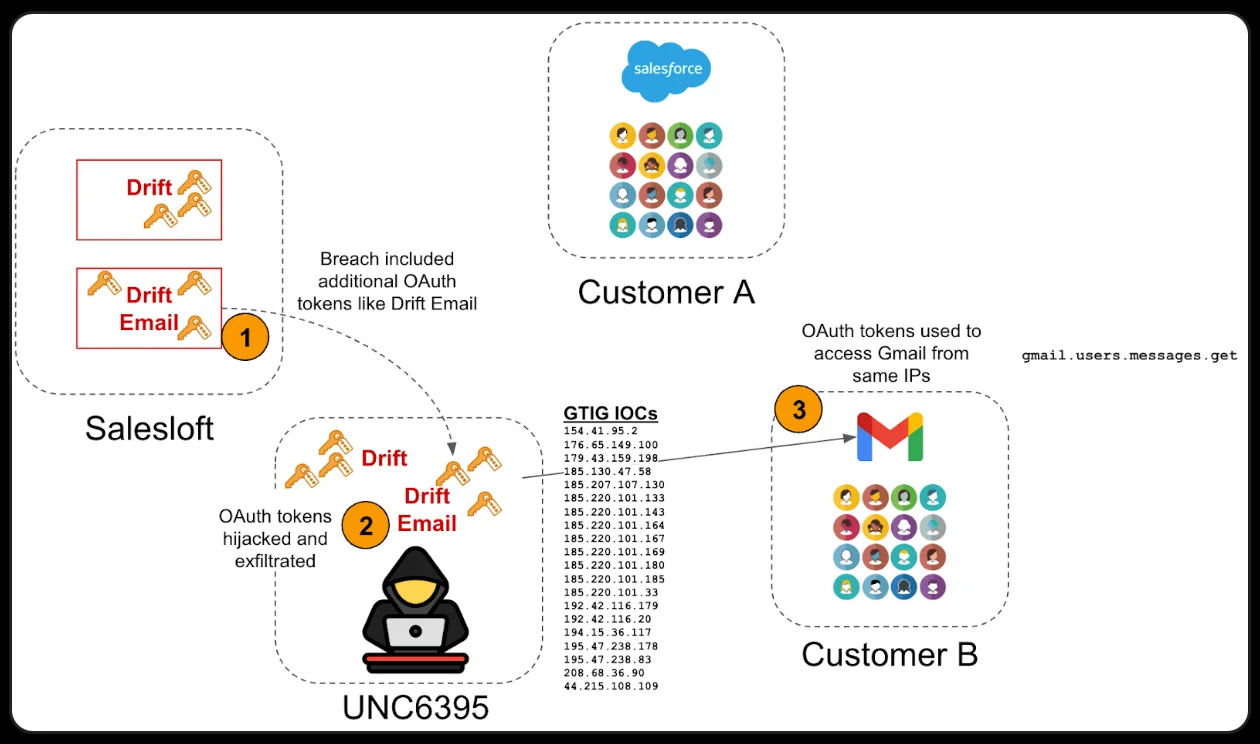
In the wake of last week’s revelation of a breach at Salesloft by a group tracked by Google as UNC6395,…
A new research project called NetMoniAI shows how AI agents might reshape network monitoring and security. Developed by a team…
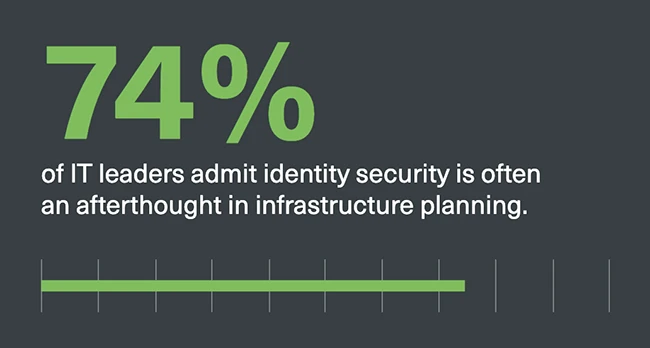
Identity has become a core pillar of cybersecurity strategy. Remote work, cloud-first adoption, and distributed supply chains have moved identity…
CISO Shift Technology | France | Remote – View job details As a CISO, you will develop and execute a…
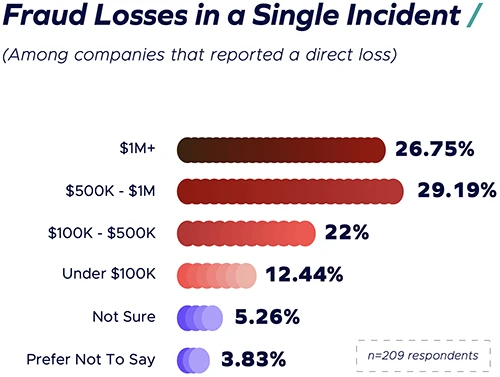
More than 80 percent of large U.S. companies were targeted by socially engineered fraud in the past year, according to…
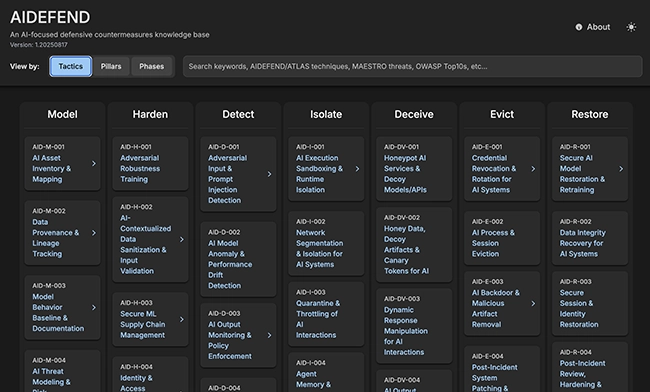
AIDEFEND (Artificial Intelligence Defense Framework) is an open knowledge base dedicated to AI security, providing defensive countermeasures and best practices…
A team of researchers from Frondeur Labs, DistributedApps.ai, and OWASP has developed a new machine learning framework designed to help…
Boards of directors are being told that cybersecurity is now central to business resilience and growth, and that they must…
There is constant pressure on security leaders to decide which controls deserve the most attention and budget. A new study…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: 300k+ Plex Media Server instances…
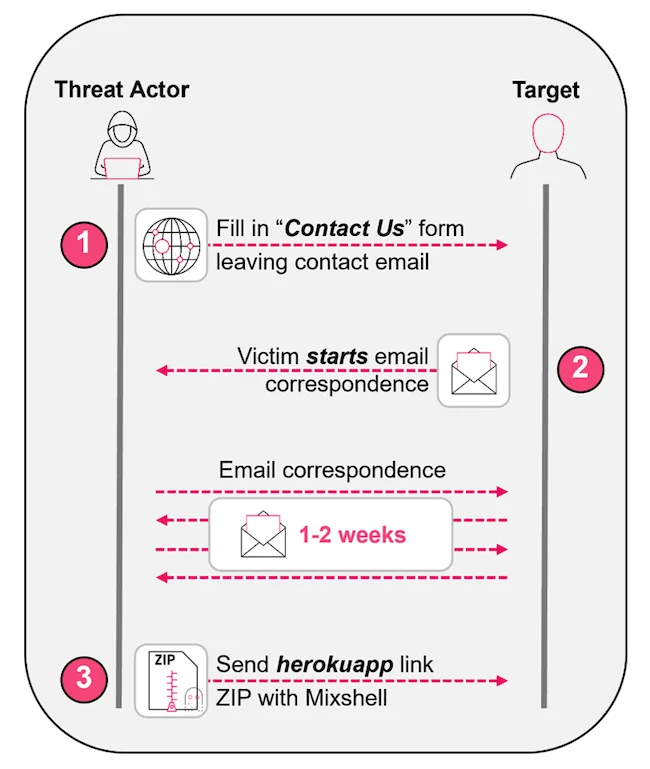
A recently uncovered phishing campaign – carefully designed to bypass security defenses and avoid detection by its intended victims –…
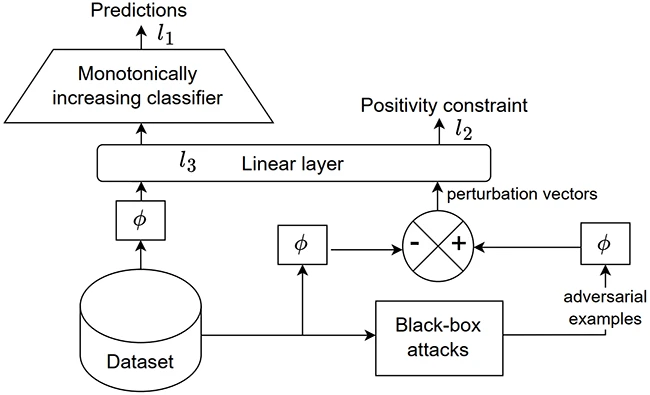
Attackers have learned how to trick machine learning malware detectors with small but clever code changes, and researchers say they…