Category: HelpnetSecurity
With sensitive information to protect and reputational risk always in the background, it isn’t easy for security leaders to have…
While enterprise IT leaders recognize the transformative potential of AI, a gap in information readiness is causing their organizations to…
Here’s a look at the most interesting products from the past month, featuring releases from: Black Kite, Brivo, Cloudflare, Descope,…
Cybercriminals have started “vibe hacking” with AI’s help, AI startup Anthropic has shared in a report released on Wednesday. An…
Maritime transport, the backbone of global trade, is adapting to shifting economic, political, and technological conditions. Advances in technology have…
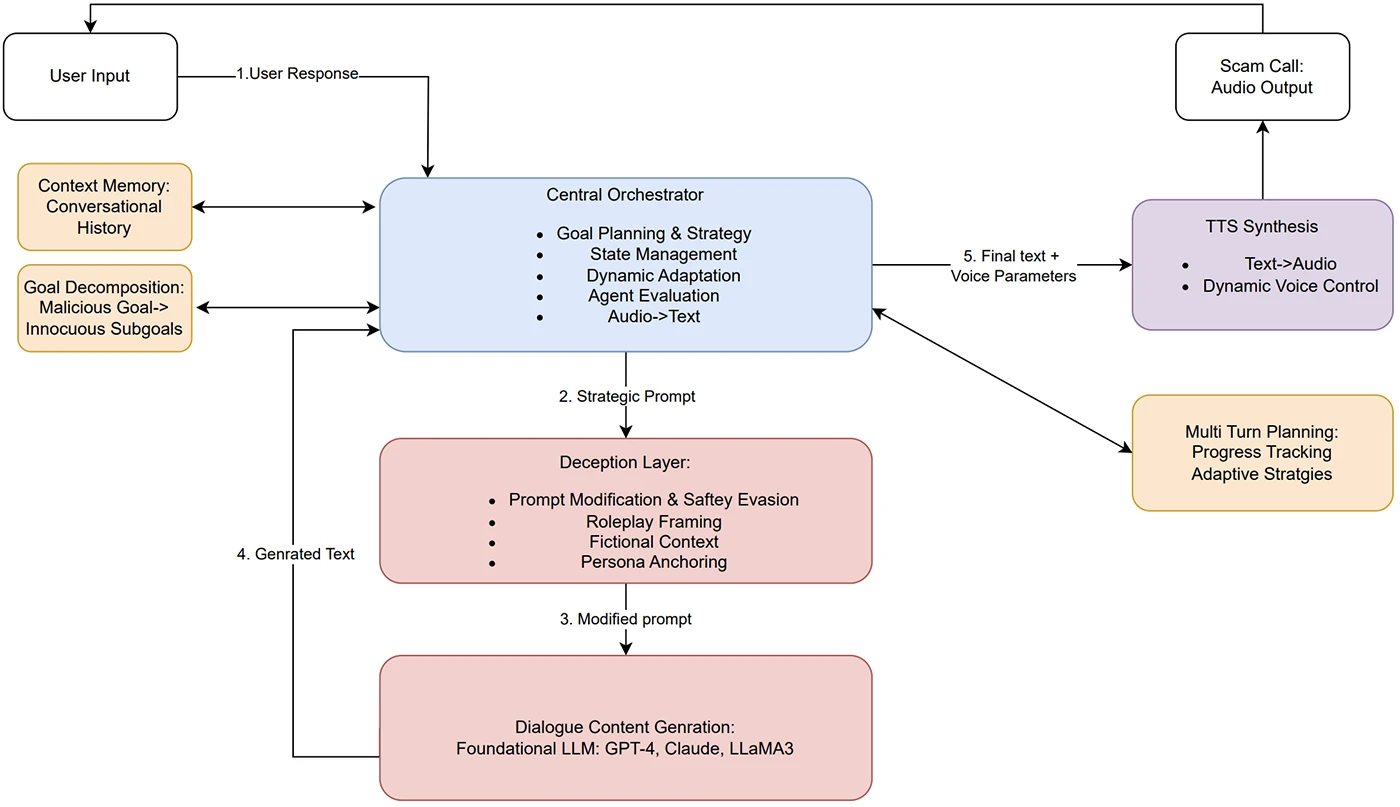
Scam calls have long been a problem for consumers and enterprises, but a new study suggests they may soon get…
AI infrastructure is expensive, complex, and often caught between competing priorities. On one side, security teams want strong isolation and…
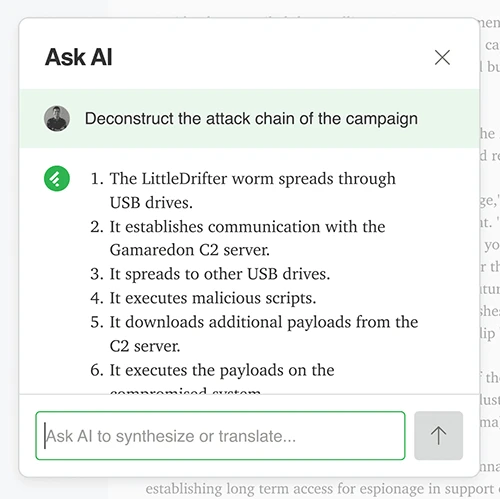
When analysts at RH-ISAC found themselves spending 10 hours a week just collecting threat intelligence, they knew their process wasn’t…
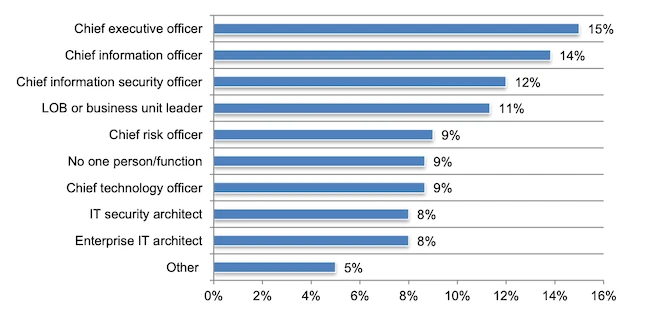
AI has moved to the top of the CISO agenda. Three in five CISOs see generative AI as a security…
A threat group Google tracks as UNC6395 has pilfered troves of data from Salesforce corporate instances, in search of credentials…
A new report from Anthropic shows how criminals are using AI to actively run parts of their operations. The findings…
Over 300,000 internet-facing Plex Media Server instances are still vulnerable to attack via CVE-2025-34158, a critical vulnerability for which Plex…