Category: HelpnetSecurity
Face morphing software can blend two people’s photos into one image, making it possible for someone to fool identity checks…
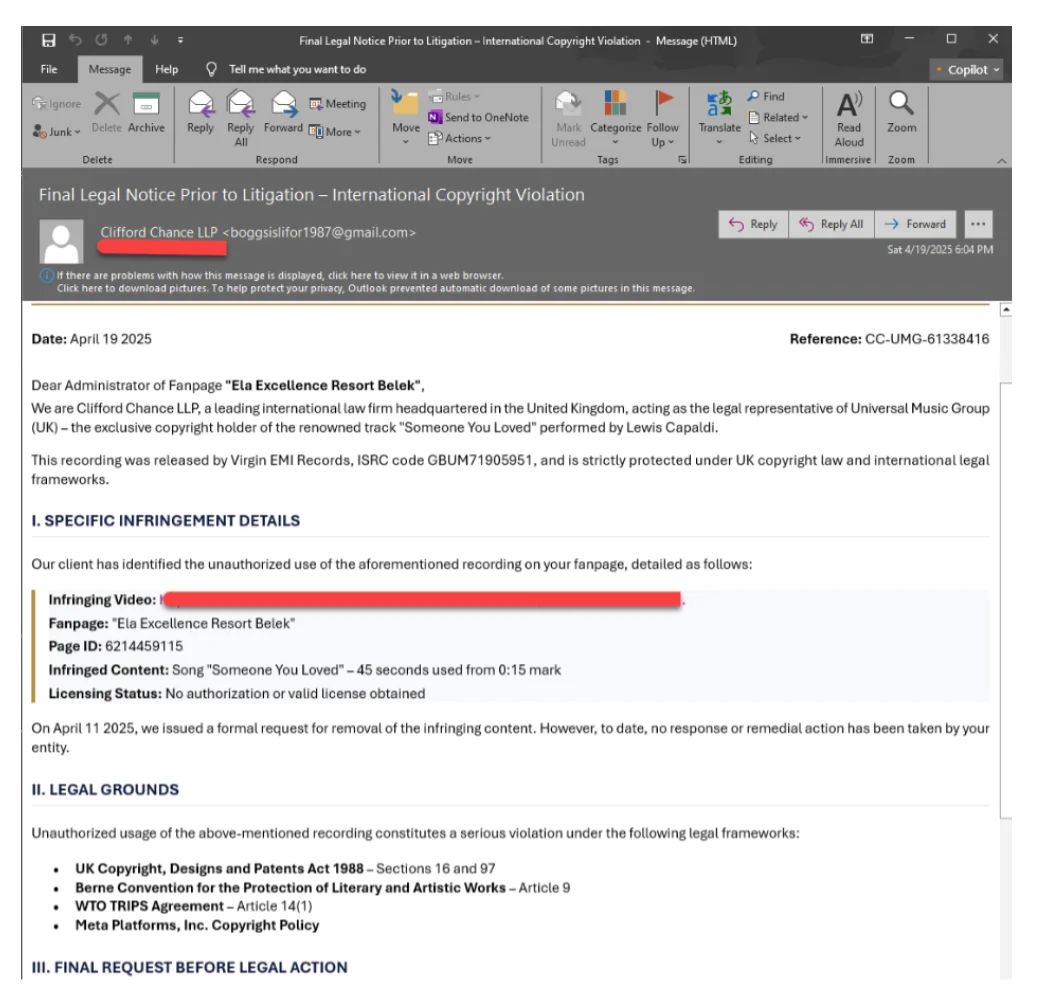
Attackers pushing the Noodlophile infostealer are targeting businesses with spear-phishing emails threatening legal action due to copyright or intellectual property…
Data Engineering for Cybersecurity sets out to bridge a gap many security teams encounter: knowing what to do with the…
AI is moving from proof-of-concept into everyday security operations. In many SOCs, it is now used to cut down alert…
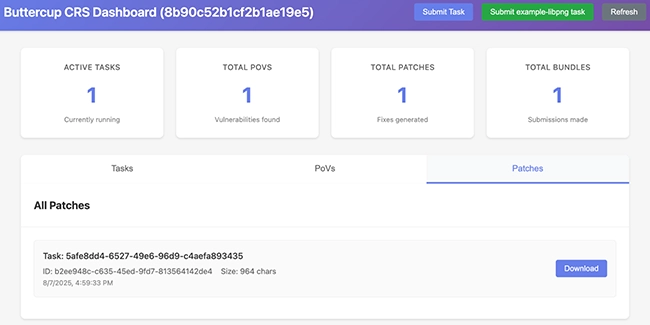
Buttercup is a free, automated, AI-powered platform that finds and fixes vulnerabilities in open-source software. Developed by Trail of Bits,…
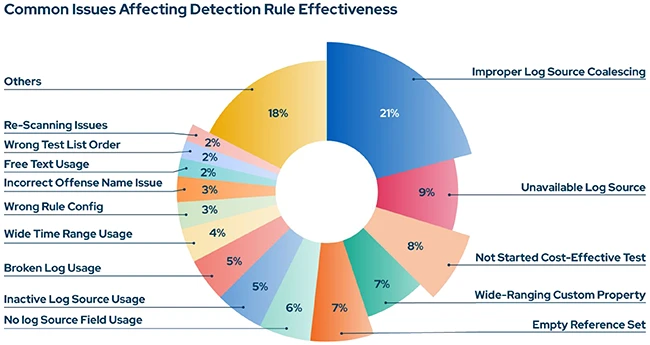
Prevention effectiveness is falling, detection gaps remain wide, and attackers are exploiting weaknesses in data protection and credentials. Data theft…
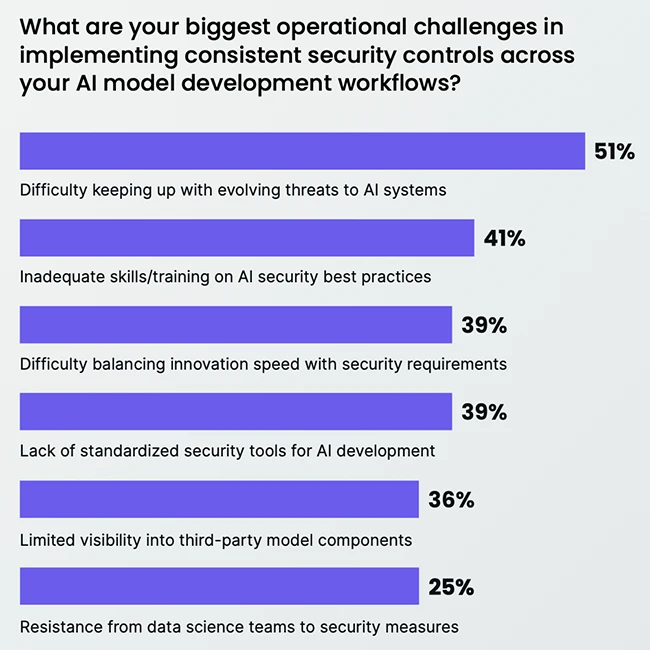
While most organizations understand the need for strong AI model governance, many are still struggling to close gaps that could…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: WinRAR zero-day was exploited by…
In this Help Net Security interview, Warren O’Driscoll, Head of Security Practice at NTT DATA UK and Ireland, discusses how…
The cyber insurance market is entering a new phase of evolution and showing early signs of maturity, according to recent…
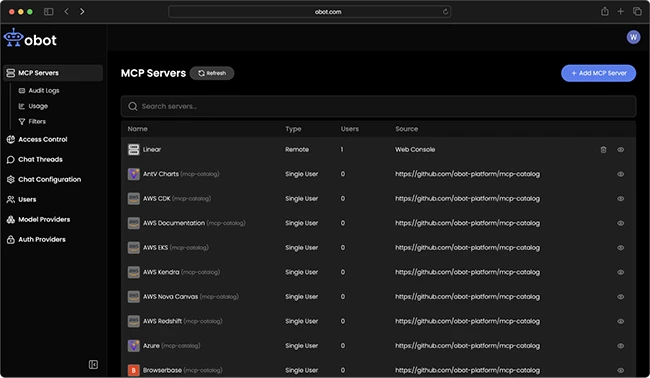
Obot MCP Gateway is a free, open-source gateway that enables IT organizations to securely manage and scale adoption of Model…
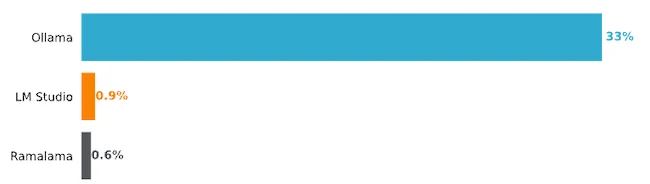
The latest Netskope findings show a 50% increase in GenAI platform usage among enterprise end-users, driven by growing employee demand…